Ukraine Under Digital Siege New Malware WRECKSTEEL Targets State Agencies
Ukrainian government agencies and critical infrastructure have been hit by a wave of cyberattacks designed to siphon off sensitive information, according to a new alert from CERT-UA. The attacks, numbering at least three, employed the previously unseen WRECKSTEEL malware, raising concerns about a potential escalation in digital warfare targeting the country.
Ukraine's Computer Emergency Response Team (CERT-UA) is sounding the alarm. They've detected at least three cyberattacks aimed at stealing sensitive data from state administration bodies and critical infrastructure.
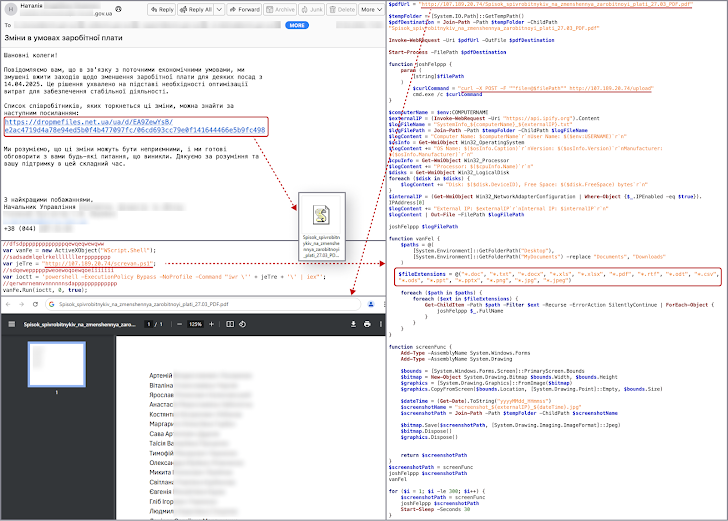
How are they doing it? According to CERT-UA, attackers are using compromised email accounts to send phishing emails. These emails contain links that appear to lead to legitimate services like DropMeFiles and Google Drive. Sometimes, the links are sneakily embedded within PDF attachments.
The emails try to trick people into clicking by creating a sense of urgency. They might claim that a Ukrainian government agency is planning salary cuts and urge the recipient to click a link to see the list of affected employees. It's a classic phishing tactic.
But here's the catch: clicking those links downloads a Visual Basic Script (VBS) loader. This loader then fetches and runs a PowerShell script. This script is designed to grab files with specific extensions and even capture screenshots.
This activity, linked to a group called UAC-0219, has been going on since at least fall 2024. Early versions used EXE files, a VBS stealer, and even a legitimate image editor called IrfanView to achieve their goals.
CERT-UA has dubbed the VBS loader and PowerShell malware "WRECKSTEEL." So far, these attacks haven't been attributed to any specific country.
Phishing Campaign Targets Defense and Aerospace
These attacks follow another recent phishing campaign targeting defense and aerospace organizations with connections to the conflict in Ukraine. The goal? To steal webmail credentials using fake login pages.
The DomainTools Investigations (DTI) team reported that the attackers seem to have built the fake login pages using Mailu, an open-source mail server software available on GitHub. Pretty clever, right?
"The focus on spoofing organizations involved in Ukraine’s defense and telecommunications infrastructure further suggests an intent to gather intelligence related to the conflict in Ukraine," DTI noted. "Notably, many of the spoofed defense, aerospace, and IT companies have provided support to Ukraine's military efforts in its conflict with Russia."
Russian-Aligned Groups Active
Several Russian-aligned groups, including UAC-0050 and UAC-0006, have also been spotted running spam campaigns for financial gain and espionage since the start of 2025. They're primarily targeting governments, defense, energy, and NGOs, spreading malware like sLoad, Remcos RAT, NetSupport RAT, and SmokeLoader.
In related news, Kaspersky recently warned that the threat actor known as Head Mare has been targeting Russian entities with PhantomPyramid malware. This malware can receive instructions from a command-and-control server and download/run additional malicious software.
Russian energy companies, industrial enterprises, and suppliers of electronic components have also been hit by phishing attacks from a group called Unicorn. They're using a VBS trojan to steal files and images from infected computers.
Operation HollowQuill: Targeting Russian Networks
And there's more. SEQRITE Labs revealed that academic, governmental, aerospace, and defense networks in Russia are being targeted by weaponized documents in a campaign called Operation HollowQuill. These attacks likely started around December 2024.
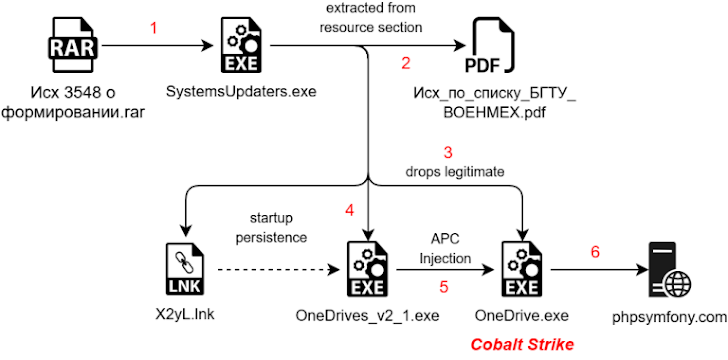
The attackers are using social engineering to trick people. They're disguising malware-laden PDFs as research invitations and official government communications to lure unsuspecting users into triggering the attack.
According to security researcher Subhajeet Singha from SEQRITE, "The threat entity delivers a malicious RAR file which contains a .NET malware dropper, which further drops a Golang-based shellcode loader along with the legitimate OneDrive application and a decoy-based PDF with a final Cobalt Strike payload."