Ukraine Under Attack New Malware Delivered Through Deceptive Excel Documents
Ukrainian organizations are once again under fire from cybercriminals, with a threat group dubbed UAC-0226 deploying the 'GIFTEDCROOK' information stealer. The Computer Emergency Response Team of Ukraine (CERT-UA) reports that attackers are using malicious Excel files to deliver the malware.
Ukraine's Computer Emergency Response Team (CERT-UA) is sounding the alarm! They've uncovered a new wave of cyberattacks hitting Ukrainian institutions, all aimed at stealing sensitive information.
According to CERT-UA, these attacks are specifically targeting military units, law enforcement, and local government bodies, especially those near the eastern border of Ukraine. So, what's the method?
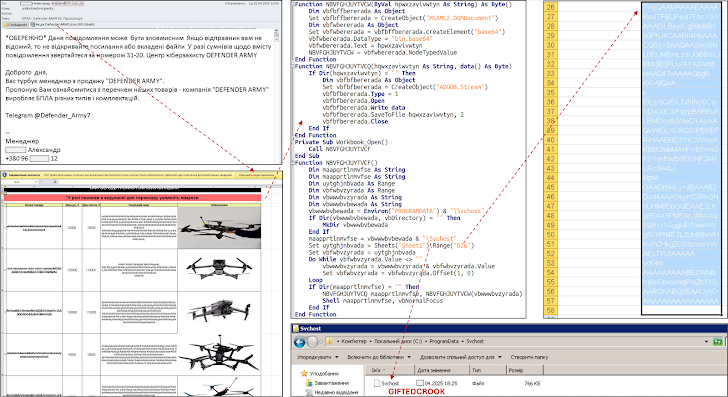
It all starts with phishing emails. These emails carry a seemingly harmless Microsoft Excel spreadsheet (XLSM file). But here's the catch: once you open it and enable macros, it unleashes two nasty pieces of malware. One is a PowerShell script pulled from a public GitHub repository called PSSW100AVB, which creates a backdoor. The other? A brand new stealer malware they're calling GIFTEDCROOK.
"The bad guys are getting crafty," CERT-UA warns. "They're using file names and email subjects that sound legitimate and relevant, like demining, administrative fines, or even compensation for damaged property."
And the real kicker? "These spreadsheets contain malicious code that, once you open the document and enable macros, turns into malware and runs without you even knowing!"
What is GIFTEDCROOK?
This GIFTEDCROOK malware, written in C/C++, is designed to steal your personal data from web browsers like Chrome, Edge, and Firefox. We're talking cookies, browsing history, and even your login credentials. Ouch!
To make matters worse, these phishing emails often come from compromised accounts, making them look even more trustworthy. CERT-UA is tracking this activity under the name UAC-0226, but they haven't pinned down a specific country responsible just yet.
RDP Attacks on the Rise
This news comes alongside another concerning trend: a suspected Russian-linked group, UNC5837, has been targeting European governments and military organizations with phishing attacks using malicious Remote Desktop Protocol (RDP) files, as reported in October 2024.
According to the Google Threat Intelligence Group (GTIG), this campaign is pretty sneaky. "Instead of just trying to take over your computer remotely, they're using the RDP connection to map your file system to their servers and run attacker-controlled applications," they explained.
CERT-UA, along with Amazon Web Services and Microsoft, previously documented this RDP campaign in October. CERT-UA calls it UAC-0215, while others believe it's the work of APT29, a hacking group linked to the Russian government.
What makes this RDP attack particularly dangerous is the likely use of PyRDP, an open-source tool that helps automate malicious tasks like stealing files and grabbing information from your clipboard (including passwords!).
"These attackers can read your drives, steal your files, capture your clipboard data, and even grab your environment variables," GTIG warned. "Their main goal seems to be spying and stealing files."
Fake CAPTCHAs and Malicious Browser Extensions
But wait, there's more! In recent months, we've also seen phishing campaigns using fake CAPTCHAs and Cloudflare Turnstile to spread Legion Loader (aka Satacom). This malware then installs a malicious browser extension called "Save to Google Drive."
"It all starts when you search for a document and end up on a malicious website," Netskope Threat Labs explained. "The downloaded document has a CAPTCHA that, once clicked, takes you through a series of redirects and eventually leads to a notification page."
This page asks you to allow notifications, and then you're redirected to another CAPTCHA. Completing that CAPTCHA redirects you *again* to a page with ClickFix-style instructions to download the document you were originally looking for.
But in reality, this whole process installs Legion Loader, which downloads and runs PowerShell scripts. These scripts then install the rogue browser extension, enable developer mode, and relaunch your browser, all without your knowledge.
The ultimate goal? To steal as much of your sensitive information as possible and send it back to the attackers. Stay safe out there!




