Toll Road Text Scam Sweeps US, China-Linked Kit Suspected
A sophisticated SMS phishing operation, potentially originating from China, has been aggressively targeting toll road users across eight US states since mid-October 2024. Security experts are raising alarms about the campaign's scale and its apparent goal of financial fraud.

Cybersecurity experts are sounding the alarm about a widespread SMS phishing (smishing) campaign that's been hitting toll road users across the U.S. since October 2024. The goal? To steal your money.
Researchers at Cisco Talos believe the attacks are coming from multiple financially motivated groups. They're all using a smishing kit created by someone named "Wang Duo Yu," according to a recent report.
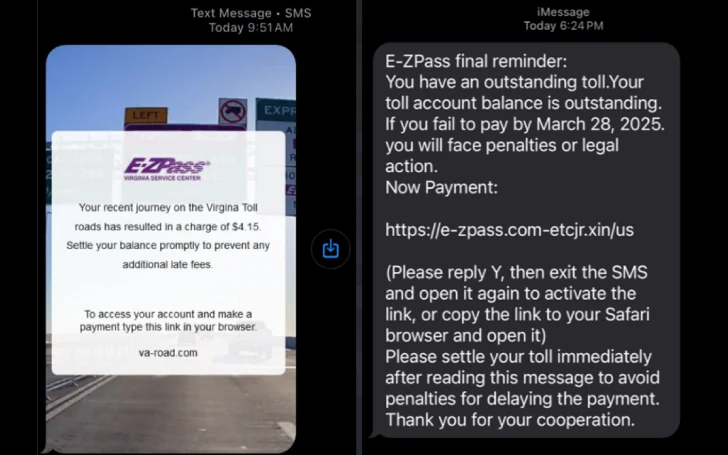
These phishing scams are impersonating electronic toll collection systems like E-ZPass. You might get a text or iMessage claiming you have an unpaid toll. It'll include a link you *definitely* shouldn't click. They're targeting people in states like Washington, Florida, Pennsylvania, Virginia, Texas, Ohio, Illinois, and Kansas.
Security journalist Brian Krebs flagged some of this activity back in January 2025, linking it to a China-based SMS phishing service called Lighthouse advertised on Telegram.
Even though Apple iMessage tries to protect you by disabling links from unknown senders, these scammers are clever. They ask you to reply with "Y" to activate the link. This tactic is similar to what's seen in other phishing kits like Darcula and Xiū gǒu.
So, what happens if you *do* click the link? First, you'll be asked to solve a fake CAPTCHA. Then, you're taken to a bogus E-ZPass page (like "ezp-va[.lcom" or "e-zpass[.]com-etcjr[.]xin"). They'll ask for your name and ZIP code to view your "bill."
Next, they push you to pay on *another* fake page. This is where they steal all your personal and financial information.
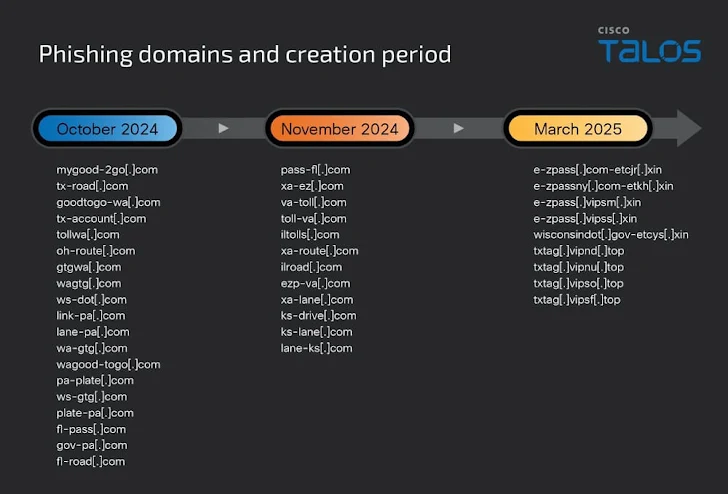
Talos points out that multiple groups are using this toll road scam, probably using Wang Duo Yu's phishing kit. They've also seen similar kits used by another Chinese cybercrime group called the Smishing Triad.
Security researcher Grant Smith says Wang Duo Yu is supposedly a computer science student in China making money on the side. Smith wrote an extensive analysis about this back in August 2024.
The Smishing Triad is known for large-scale smishing attacks, especially targeting postal services in over 120 countries. They use fake package delivery notices to trick people into clicking links and handing over their financial info for a bogus redelivery fee. See this report.
These scammers have even tried to add victims' card details to mobile wallets to steal funds using a technique called Ghost Tap. More information on this can be found here.
Here's the really nasty part: the phishing kits are backdoored. This means the creators are also stealing the credit card info you enter. It's called double theft.
"Wang Duo Yu has created and designed specific smishing kits and sells access to them on Telegram," Talos explained. "Kits are priced at $50 for a full-feature development, $30 for proxy development (if you have your own domain and server), $20 for version updates, and $20 for support."
As of March 2025, this e-crime group seems focused on a new Lighthouse phishing kit that targets banks and financial institutions in Australia and Asia-Pacific, according to Silent Push.
These guys even claim to have "300+ front desk staff worldwide" to help with the fraud and cashing out the stolen money.
"Smishing Triad is also selling its phishing kits to other malicious actors via Telegram," said Silent Push. "This makes it difficult to attribute the kits to one specific group."
A report last month from PRODAFT revealed that Lighthouse shares tactics with other phishing kits like Lucid and Darcula. PRODAFT is tracking Wang Duo Yu (aka Lao Wang) as LARVA-241.
"Attacks using Lucid and Darcula show Lighthouse (Lao Wang / Wang Duo Yu) has similar targeting, landing pages, and domain creation patterns as the XinXin group," PRODAFT noted.