Suspected Pakistan-Backed Hackers Hit India with New CurlBack RAT
Indian organizations are under renewed assault from a threat group believed to be operating out of Pakistan. Security researchers have uncovered a campaign deploying a range of remote access trojans, including the familiar Xeno RAT and Spark RAT, alongside a newly discovered malware family dubbed CurlBack RAT.

Security researchers have spotted a threat group with suspected ties to Pakistan actively targeting various sectors in India. They're deploying a range of remote access trojans (RATs), including Xeno RAT, Spark RAT, and a brand-new malware family dubbed CurlBack RAT.
According to SEQRITE's findings from December 2024, the hackers are setting their sights on Indian entities within the railway, oil and gas, and external affairs ministries. This marks a notable expansion from their previous targets, which included government, defense, maritime sectors, and universities.
"We're seeing a key change in their tactics," explains security researcher Sathwik Ram Prakki from SEQRITE. "They've moved away from using HTML Application (HTA) files and are now primarily using Microsoft Installer (MSI) packages as an initial entry point."
This group is suspected to be SideCopy, believed to be a sub-cluster of Transparent Tribe (also known as APT36). SideCopy has been active since at least 2019, and gets its name from mimicking the attack methods of another group, SideWinder, to deliver their malicious software.
Back in June 2024, SEQRITE pointed out SideCopy's use of cleverly hidden HTA files, a trick previously seen in SideWinder attacks. These files even contained references to URLs hosting RTF files, also linked to SideWinder.
These attacks often culminated in the deployment of Action RAT and ReverseRAT, two well-known malware families associated with SideCopy. Other malicious tools included Cheex (for stealing documents and images), a USB copier (for extracting data from connected drives), and a .NET-based RAT called Geta, capable of executing a whopping 30 commands from a remote server.
Notably, Geta RAT can steal browser data (accounts, profiles, and cookies) from both Firefox and Chromium-based browsers, a feature lifted from AsyncRAT.
"While APT36 primarily focuses on Linux systems, SideCopy is targeting Windows systems and constantly adding new weapons to its arsenal," SEQRITE highlighted.
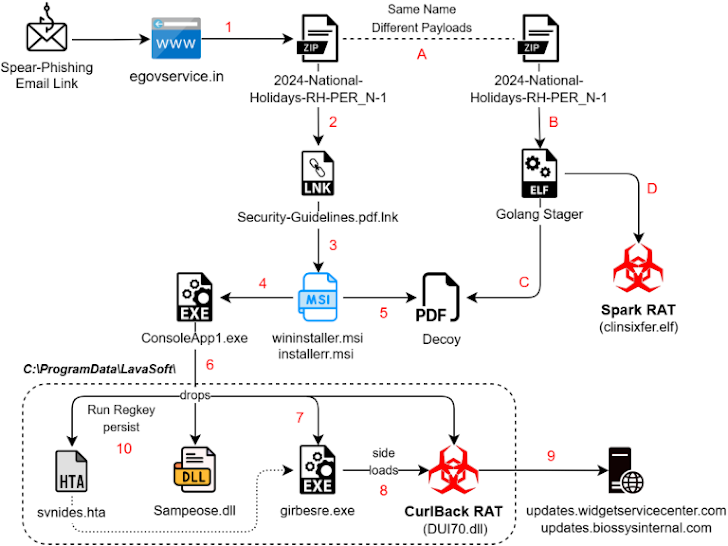
These latest findings show that SideCopy is becoming increasingly sophisticated, relying heavily on email-based phishing to spread malware. The malicious emails often contain tempting attachments, such as holiday lists for railway employees or cybersecurity guidelines supposedly issued by Hindustan Petroleum Corporation Limited (HPCL).
One particularly interesting operation targets both Windows and Linux systems, ultimately deploying Spark RAT (a cross-platform RAT) and the new Windows-based CurlBack RAT. CurlBack RAT can collect system information, download files, execute commands, escalate privileges, and list user accounts.
Another observed tactic involves using decoy files to kick off a multi-stage infection, ultimately leading to the installation of a customized version of Xeno RAT, which includes basic string manipulation techniques.
SEQRITE concludes: "The group has moved from using HTA files to MSI packages as a primary delivery method and continues to employ advanced techniques like DLL side-loading, reflective loading, and AES decryption via PowerShell."
"They're also using customized open-source tools like Xeno RAT and Spark RAT, along with the newly discovered CurlBack RAT. Compromised domains and fake websites are being used for credential phishing and hosting malicious payloads, demonstrating the group's ongoing efforts to improve persistence and avoid detection."