SuperCard X Malware Turns Androids into NFC Fraud Machines
A sophisticated Android malware platform called SuperCard X is enabling a new wave of contactless payment fraud. This Malware-as-a-Service (MaaS) allows criminals to exploit vulnerabilities in near-field communication (NFC) technology, potentially draining cash from ATMs and compromising point-of-sale systems.

A new malware-as-a-service (MaaS) platform called SuperCard X has emerged, and it's capable of some seriously sneaky stuff. It uses near-field communication (NFC) relay attacks to let criminals make fraudulent cash withdrawals.
Cleafy, a fraud prevention firm, discovered this active campaign targeting bank and card issuer customers in Italy. They believe the platform is being advertised on Telegram channels.
So, how does it work? According to security researchers Federico Valentini, Alessandro Strino, and Michele Roviello, SuperCard X combines social engineering (think smishing and phone calls), malicious app installation, and NFC data interception for highly effective fraud. Read their full analysis here.
How the Attack Unfolds
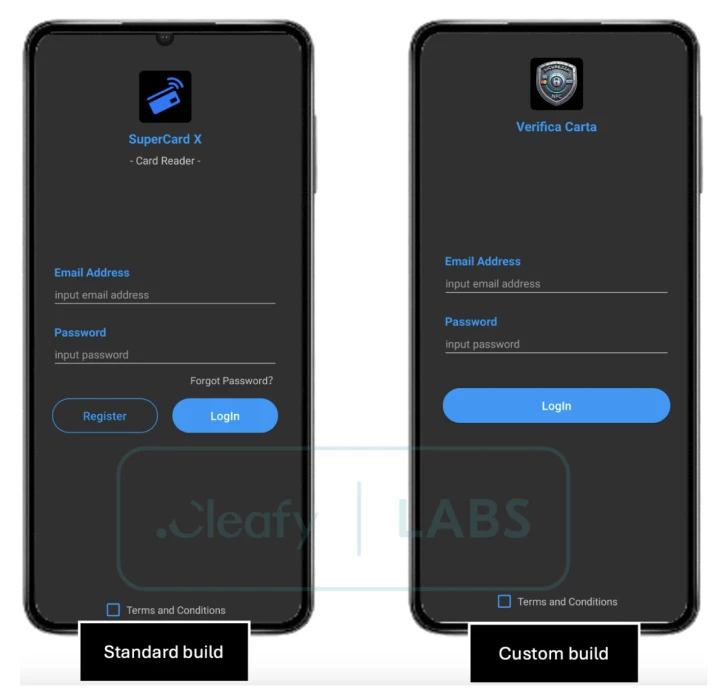
This Android malware, reportedly the work of a Chinese-speaking group, is spread through bogus apps. Victims are tricked into installing them via SMS or WhatsApp messages. Here are a few of the apps to watch out for:
- Verifica Carta (io.dxpay.remotenfc.supercard11)
- SuperCard X (io.dxpay.remotenfc.supercard)
- KingCard NFC (io.dxpay.remotenfc.supercard)
These messages often pretend to be bank security alerts, creating a sense of urgency and prompting people to call a specific number.
Then comes the tricky part: a Telephone-Oriented Attack Delivery (TOAD). The attackers convince victims to install the app, claiming it's security software. They've also been known to sweet-talk victims into revealing their PINs and removing card limits, making it even easier to steal funds.
The NFC Relay Technique
The heart of this operation is a new NFC relay technique. It allows attackers to fraudulently authorize payments at point-of-sale (PoS) terminals and ATM withdrawals by intercepting and relaying NFC communications from infected devices.
Basically, the attackers get victims to hold their debit or credit card near their phone. The SuperCard X malware secretly grabs the card details and sends them to a server. Then, the attackers use that info on their own device to make unauthorized transactions.
There are two key apps involved: a "Reader" app on the victim's phone to capture the NFC data, and a "Tapper" app on the attacker's device to receive the data. These apps communicate using HTTP, and the criminals need to be logged in to the SuperCard X platform.
Victims are even instructed to enter login credentials (provided during the phone call) into the app. This connects the victim's device to the attacker's "Tapper" instance, enabling the card data relay. The "Tapper" app can then mimic the victim's card, fooling PoS terminals and ATMs.
What to Watch Out For
Cleafy noticed that the "Reader" malware has slightly different login screens, suggesting that affiliates can customize the campaigns. SuperCard X also uses mutual TLS (mTLS) to secure communication with its command-and-control (C2) infrastructure.
Google is aware of these phone call-based scams and is reportedly working on a feature to block users from installing apps from unknown sources and granting accessibility permissions. More on that here.
How to Stay Safe
While there's no evidence of SuperCard X on the Google Play Store, be extra careful when downloading apps. Check the descriptions, permissions, and reviews. And keep Google Play Protect enabled!
The researchers at Cleafy sum it up well: "This novel campaign introduces a significant financial risk that extends beyond the conventional targets of banking institutions to affect payment providers and credit card issuers directly."
They add, "The innovative combination of malware and NFC relay empowers attackers to perform fraudulent cash-outs with debit and credit cards. This method demonstrates high efficacy, especially when targeting contactless ATM withdrawals."