Stolen SpotBugs Token Triggered Widespread GitHub Supply Chain Attack
A GitHub supply chain attack that initially impacted Coinbase and later spread to users of the "tj-actions/changed-files" Action has been traced back to a compromised personal access token (PAT) belonging to the SpotBugs project. The theft of this PAT appears to be the root cause of the cascading attack.

Remember that cascading supply chain attack that initially hit Coinbase? Well, it turns out the rabbit hole goes even deeper. What started as a targeted attack against users of the "tj-actions/changed-files" GitHub Action has been traced back to a stolen personal access token (PAT) linked to SpotBugs. Think of PATs as digital keys – and this one was compromised.
According to Palo Alto Networks Unit 42, the attackers first gained entry by exploiting the GitHub Actions workflow of SpotBugs, a widely used open-source tool for finding bugs in code. "This allowed them to move around between SpotBugs repositories, ultimately gaining access to reviewdog," they explained in a recent update.
Get this: the malicious activity seems to have started way back in late November 2024, although the actual attack on Coinbase didn't happen until March 2025. So, what was going on in the meantime?
Unit 42's investigation revealed that the "reviewdog/action-setup" GitHub Action was compromised due to a leaked PAT belonging to the project's maintainer. This allowed the attackers to slip in a malicious version of "reviewdog/action-setup," which was then picked up by "tj-actions/changed-files" because it was listed as a dependency via the "tj-actions/eslint-changed-files" action. It's like a chain reaction of vulnerabilities!
And here's where SpotBugs comes back into the picture: the maintainer of "reviewdog/action-setup" was also involved in SpotBugs.
Reportedly, the attackers managed to sneak a malicious GitHub Actions workflow file into the "spotbugs/spotbugs" repository using the throwaway username "jurkaofavak." When this workflow was executed, it caused the maintainer's PAT to be leaked. Busted!
The theory is that this same PAT was used to access both "spotbugs/spotbugs" and "reviewdog/action-setup," meaning the leaked PAT could be used to tamper with "reviewdog/action-setup." A real house of cards, right?
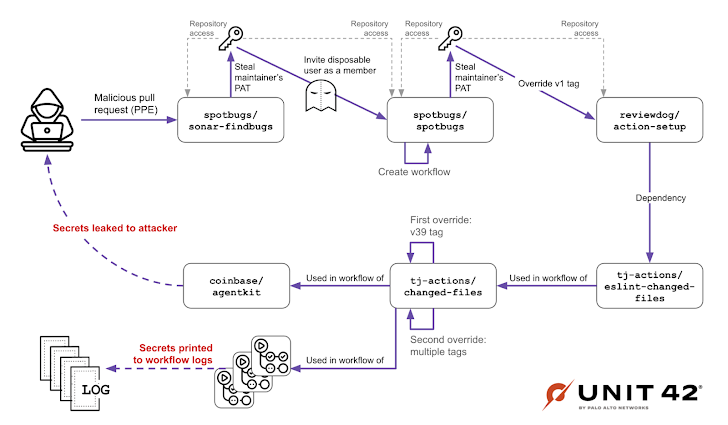
"The attacker somehow had an account with write permission in spotbugs/spotbugs, which they were able to use to push a branch to the repository and access the CI secrets," Unit 42 noted. So how did "jurkaofavak" get those write permissions?
Turns out, one of the project maintainers *invited* "jurkaofavak" to become a member of the repository back on March 11, 2025. Yikes!
In other words, the attackers managed to snag the SpotBugs repository's PAT to invite "jurkaofavak" to become a member. The cybersecurity company believes this was done by creating a fork of the "spotbugs/sonar-findbugs" repository and submitting a pull request under the username "randolzfow."
Unit 42 explained that on November 28, 2024, "[the SpotBugs maintainer] modified one of the 'spotbugs/sonar-findbugs workflows to use their own PAT, as they were having technical difficulties in a part of their CI/CD process."
Then, on December 6, 2024, "the attacker submitted a malicious pull request to spotbugs/sonar-findbugs, which exploited a GitHub Actions workflow that used the pull_request_target trigger."
The "pull_request_target" trigger in GitHub Actions allows workflows running from forks to access secrets – in this case, the PAT – leading to a "poisoned pipeline execution attack" (PPE). Nasty stuff.
The SpotBugs maintainer has since confirmed that the PAT used in the workflow was the same one later used to invite "jurkaofavak" to the "spotbugs/spotbugs" repository. They've also revoked all their tokens and PATs to prevent further access. Lesson learned (hopefully!).
The big question is: what happened during those three months between when the attackers stole the SpotBugs maintainer's PAT and when they actually used it? It's suspected that they were carefully watching projects dependent on "tj-actions/changed-files," waiting for the perfect, high-value target like Coinbase.
As Unit 42 researchers put it: "Having invested months of effort and after achieving so much, why did the attackers print the secrets to logs, and in doing so, also reveal their attack?" It's a puzzle that remains to be fully solved.




