SourceForge Users Targeted with Crypto Miners and Clipboard Hijackers
Hackers are exploiting SourceForge, a well-known software repository, to spread cryptocurrency miners and 'clipper' malware. Disguised as cracked versions of popular programs like Microsoft Office, these malicious downloads can secretly generate cryptocurrency or steal cryptocurrency addresses copied to the clipboard, redirecting funds to attacker-controlled wallets.
Bad news for bargain hunters: Cybersecurity researchers have spotted hackers using SourceForge, a well-known software repository, to distribute malware. They're disguising it as cracked versions of popular apps, like Microsoft Office. So, that "free" software might cost you more than you think!
Kaspersky, the cybersecurity firm, dug into one specific project called "officepackage" on SourceForge. "It looks harmless at first glance," they reported. "It seems to just contain Microsoft Office add-ins copied from a legitimate GitHub project." They added that the description and contents were also lifted from GitHub.
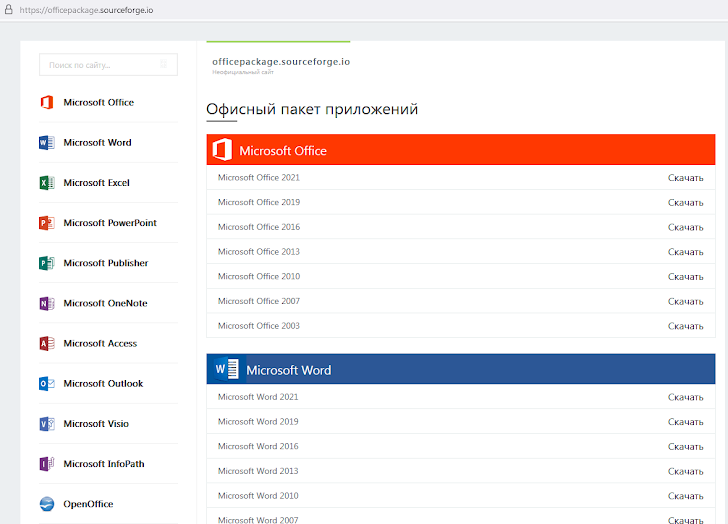
Here's the catch: While every project on SourceForge gets its own subdomain (like "projectname.sourceforge.io"), the "officepackage" one – officepackage.sourceforge[.]io – shows a list of Microsoft Office apps with download links, all in Russian. Suspicious, right?
And it gets worse. Hovering over the download button? It *looks* like a safe SourceForge link. But click it, and you're redirected to a totally different site on "taplink[.]cc" with *another* download button. Classic bait-and-switch.
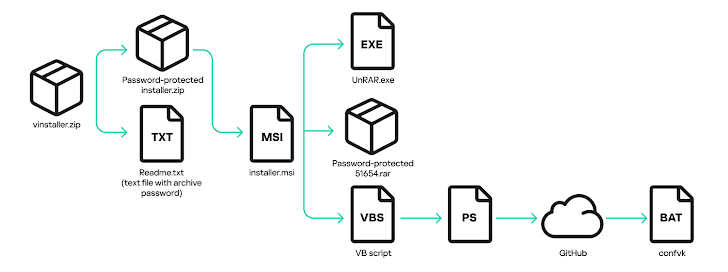
If you fall for it and click *that* download button, you get a 7MB ZIP file called "vinstaller.zip." Inside, there's *another* password-protected ZIP file ("installer.zip") and a text file with the password. Talk about layers!
Inside *that* ZIP file is an MSI installer. This installer sets up several files: a console archive utility called "UnRAR.exe," a RAR archive, and a Visual Basic (VB) script. That VB script then runs a PowerShell command to grab a batch file ("confvk") from GitHub.
Kaspersky explains that this "confvk" file contains the password for the RAR archive, unpacks the *real* malicious files, and kicks off the next stage of the attack.
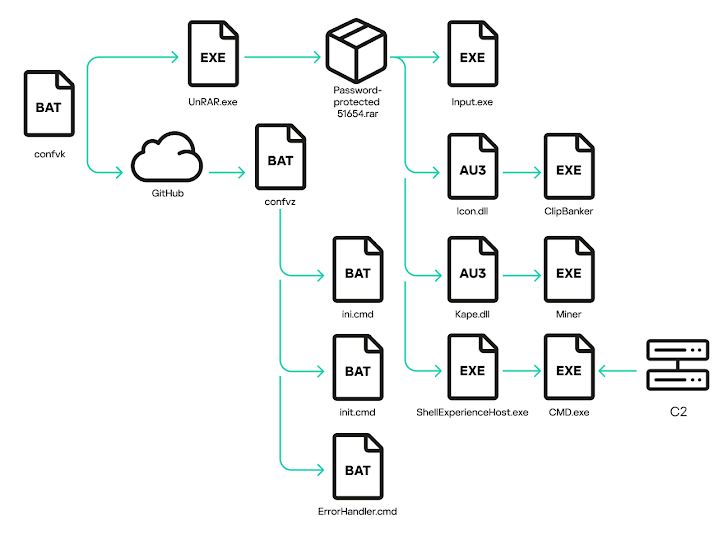
That batch file also runs two PowerShell scripts. One sends your system info to the attackers using the Telegram API. The other downloads *another* batch script, which finally unleashes the miner and clipper malware (also known as ClipBanker). These clippers silently swap out crypto wallet addresses in your clipboard when you copy and paste, so you end up sending crypto to the attacker instead of your intended recipient.
And there's more! The attack also drops "ShellExperienceHost.exe" (a version of netcat), which creates an encrypted connection back to the attacker's server. Plus, the "confvk" batch file makes another file, "ErrorHandler.cmd," containing a PowerShell script that grabs and runs text strings via the Telegram API.
The fact that the whole thing is in Russian suggests the attackers are targeting Russian speakers. Data shows that 90% of the victims are likely in Russia, with over 4,600 users hit between January and March.
Because these fake SourceForge pages are indexed by search engines, it's likely that Russian users searching for Microsoft Office on Yandex (a popular Russian search engine) are the main target.
"Attackers are preying on users looking for ways to download apps outside official channels," Kaspersky warns. "While the immediate goal is cryptocurrency theft, they could easily sell access to compromised systems to even more dangerous actors."
This discovery comes on the heels of another campaign where attackers are spreading malware called TookPS through fake websites that look like the DeepSeek AI chatbot and other software.
Malwarebytes pointed out that these fake sites, like deepseek-ai-soft[.]com, often show up in sponsored Google search results.
TookPS downloads and runs PowerShell scripts that give attackers remote access via SSH. It also drops a modified version of a trojan called TeviRat. The goal? Total control of your computer.
Kaspersky notes that "The sample [...] uses DLL sideloading to modify and deploy the TeamViewer remote access software onto infected devices," adding "In simple terms, the attackers place a malicious library in the same folder as TeamViewer, which alters the software's default behavior and settings, hiding it from the user and providing the attackers with covert remote access."
And, just recently, researchers found malicious Google ads for RVTools (a VMware utility) that delivered a hacked version loaded with ThunderShell (aka SMOKEDHAM), a remote access tool. It's a reminder that malicious ads are still a big problem.
Field Effect describes ThunderShell as "a publicly available post-exploitation framework designed for red teaming and penetration testing," that "provides a command-and-control (C2) environment that allows operators to execute commands on compromised machines through a PowerShell-based agent."

