SentinelOne Says Chinese Hackers Targeted Its Systems and Clients
A China-linked hacking group known as PurpleHaze attempted to infiltrate SentinelOne's infrastructure and the networks of some of its most important customers, the cybersecurity firm disclosed today. The reconnaissance attempts suggest a potential espionage campaign.

Cybersecurity company SentinelOne recently revealed that a China-linked hacking group, which they're calling PurpleHaze, tried to snoop around their systems and those of some of their most important customers. It seems nobody's immune to these attacks!
"We noticed this group when they broke into an organization that used to handle hardware logistics for our employees," explained SentinelOne's security researchers Tom Hegel, Aleksandar Milenkoski, and Jim Walter in their report.
So, who is PurpleHaze? They're believed to be connected to another group backed by the Chinese government, known as APT15 (also known by a whole bunch of other names like Flea, Nylon Typhoon, and Vixen Panda). These guys are busy!
Back in October 2024, PurpleHaze also went after a South Asian government organization, using a sneaky network setup and a Windows backdoor called GoReShell.
This GoReShell backdoor is interesting. It uses an open-source tool called reverse_ssh to create secret connections back to the hackers.
"These kinds of networks are becoming more popular with these groups," the researchers noted. "They're quick to set up and change, making it harder to track them and figure out who's behind the attacks."
Turns out, that same South Asian government target was hit before, back in June 2024, with a backdoor called ShadowPad (also known as PoisonPlug). This is a popular tool among Chinese hacking groups, considered the successor to PlugX.
Here's the twist: ShadowPad has also been used to spread ransomware lately, so it's not entirely clear what the hackers' goals were. The ShadowPad code was hidden using a special tool called ScatterBrain.
It's still unclear how the June attack and the PurpleHaze attacks are related, but investigators suspect it might be the same people.
The ScatterBrain-obfuscated ShadowPad has been used in attacks against over 70 organizations in different sectors after exploiting a vulnerability in Check Point devices.
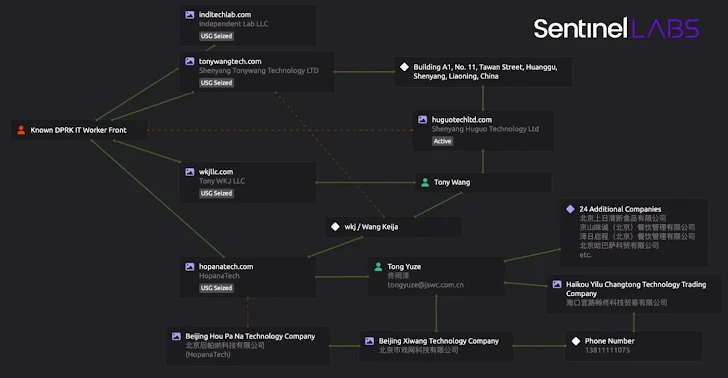
One of the victims in these attacks was the company managing hardware for SentinelOne employees. Fortunately, SentinelOne says they didn't find any evidence that their own systems were compromised as a result.
But wait, there's more! SentinelOne also spotted North Korean hackers trying to get jobs at the company, using fake profiles and applications. They even targeted the SentinelLabs team!
Finally, ransomware groups have been targeting SentinelOne and other security companies, trying to figure out how to get past their defenses.
There's a whole underground market where people buy and sell access to these security tools, using messaging apps and forums.
"There are even services offering 'EDR Testing-as-a-Service,' where hackers can test their malware against different security systems," the researchers explained.
"These services let attackers test their code without getting caught, making it much easier to succeed in real attacks."
One ransomware group, called Nitrogen, is taking things to a new level. They're pretending to be real companies to buy licenses for security products.
They create fake websites, email addresses, and infrastructure to look like legitimate businesses, allowing them to purchase legitimate licenses for security products.
"This social engineering is done with precision," the researchers said. "Nitrogen usually targets small resellers with weak verification processes, so they can slip through the cracks."