Russian Military Targeted by Android Spyware Masquerading as Mapping App
A new Android spyware campaign is targeting Russian military personnel, researchers warn. The malware is cleverly disguised as a legitimate Alpine Quest mapping application, potentially compromising sensitive data on infected devices.
Cybersecurity researchers have uncovered a new malicious campaign targeting Russian military personnel. The attackers are distributing Android spyware disguised as the popular Alpine Quest mapping software.
According to Doctor Web, a Russian cybersecurity firm, "The attackers hide this trojan inside modified Alpine Quest mapping software and distribute it in various ways, including through one of the Russian Android app catalogs." You can read their full analysis here.
The trojan is being found embedded in older versions of the software, offered as a "free" version of Alpine Quest Pro, which normally comes with advanced features.
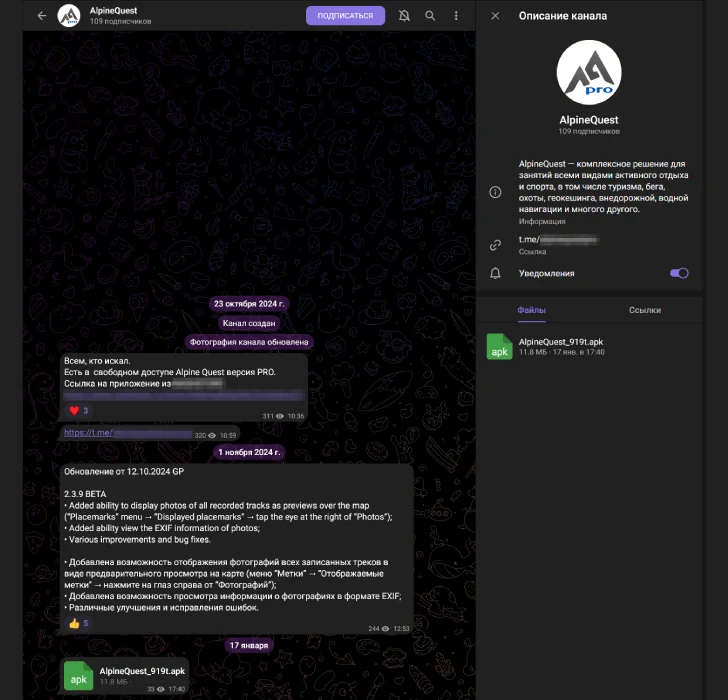
Doctor Web also discovered the malware, which they've dubbed Android.Spy.1292.origin, being spread as an APK file through a fake Telegram channel.
Initially, the Telegram channel provided a link to download the app from a Russian app catalog. However, the attackers later switched to distributing the infected version directly as an APK, disguised as an app update.
What makes this attack particularly alarming? Alpine Quest is used by Russian military personnel in the Special Military Operation zone. This makes it a prime target for those seeking sensitive information.
Once installed, the malicious app looks and functions just like the real thing. This allows it to stay hidden while it silently collects data, including:
- Mobile phone number and associated accounts
- Contact lists
- Current date and geolocation
- Information about stored files
- App version
The spyware doesn't stop there. It sends the victim's location to a Telegram bot whenever it changes. It can also download and run additional modules, allowing it to steal files, especially those sent via Telegram and WhatsApp.
"Android.Spy.1292.origin not only allows user locations to be monitored but also confidential files to be hijacked," Doctor Web warns. "In addition, its functionality can be expanded via the download of new modules, which allows it to then execute a wider spectrum of malicious tasks."
So, how can you protect yourself? Only download Android apps from trusted app marketplaces. And be extremely wary of downloading "free" versions of paid software from suspicious sources.
Russian Organizations Targeted by New Windows Backdoor
And the threats don't stop there. Kaspersky has revealed that several large Russian organizations in government, finance, and industry have been targeted by a sophisticated backdoor. This backdoor is cleverly disguised as an update for ViPNet, a secure networking software.
"The backdoor targets computers connected to ViPNet networks," Kaspersky reports. "The backdoor was distributed inside LZH archives with a structure typical of updates for the software product in question."
The archive contains a malicious executable ("msinfo32.exe") that loads an encrypted payload.
"The loader processes the contents of the file to load the backdoor into memory," Kaspersky explains. "This backdoor is versatile: it can connect to a C2 server via TCP, allowing the attacker to steal files from infected computers and launch additional malicious components."




