Russian Hackers Use Wine Theme to Target European Diplomats
A sophisticated phishing campaign, attributed to the Russian state-backed APT29 group, is using invitations to wine-tasting events as bait to infect European diplomats. Researchers have uncovered a new malware loader, dubbed GRAPELOADER, alongside a variant of WINELOADER in this ongoing operation.

A Russian hacking group, suspected of working for the Kremlin, is using a clever phishing campaign to target European diplomatic entities. They're using a new version of malware called WINELOADER and a previously unknown malware loader dubbed GRAPELOADER.
Check Point researchers uncovered this nasty scheme. They explain that while WINELOADER acts as a modular backdoor in the later stages of an attack, GRAPELOADER is the new kid on the block, used to gather intel on your system, maintain persistence, and ultimately deliver the malicious payload.
"Think of GRAPELOADER as a stealthier, more advanced version of WINELOADER, designed to evade detection," Check Point researchers noted.
Remember WINELOADER? It first surfaced back in February, using wine-tasting invitations as bait. Initially, it was linked to a group called SPIKEDWINE, but later, Google's Mandiant team tied it to APT29, also known as Cozy Bear or Midnight Blizzard – a hacking group with ties to Russia's Foreign Intelligence Service (SVR).
How the Attack Works
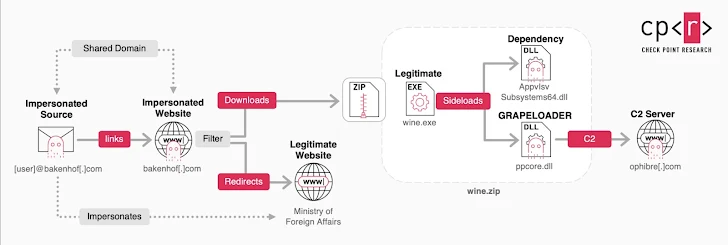
So, what's the latest tactic? The attackers send out fake email invites to wine-tasting events, supposedly from a European Ministry of Foreign Affairs. These emails trick recipients into clicking a link, which then downloads a malicious ZIP archive ("wine.zip") containing GRAPELOADER. The emails appear to originate from the domains bakenhof[.]com and silry[.]com.
The campaign is primarily targeting Ministries of Foreign Affairs in various European countries, along with embassies. There's also evidence that diplomats in the Middle East may be in the crosshairs.
Inside the ZIP archive are three files:
- A DLL ("AppvIsvSubsystems64.dll") - A legitimate dependency.
- A PowerPoint executable ("wine.exe") - Exploited for DLL side-loading.
- A malicious DLL ("ppcore.dll") - The GRAPELOADER itself.
The attack uses a technique called DLL side-loading, where the legitimate PowerPoint executable is tricked into loading the malicious DLL. This allows the GRAPELOADER to be deployed.
To stick around, the malware modifies the Windows Registry, ensuring that the "wine.exe" file (and therefore the malware) is launched every time the system restarts.
GRAPELOADER: Stealth and Data Gathering
GRAPELOADER isn't just about getting in; it's about staying hidden. It uses anti-analysis techniques like string obfuscation and runtime API resolving to make it harder to detect. It also collects basic information about the infected computer and sends it to a remote server to retrieve the next stage of the attack.
While the exact nature of the final payload remains unclear, Check Point believes that GRAPELOADER ultimately leads to the deployment of the WINELOADER backdoor.
Gamaredon's USB-Spreading Malware
But wait, there's more! Around the same time, HarfangLab uncovered details about Gamaredon's PteroLNK VBScript malware. This nasty piece of code, also linked to Russia, infects all connected USB drives with malicious VBScript or PowerShell files. ESET reported on this back in September 2024.
Think of it this way: every time you plug in a USB drive, this malware tries to copy itself onto it using shortcut (LNK) files. Clicking on these shortcuts launches the malware, which then downloads even more malicious payloads.
HarfangLab describes PteroLNK VBScript files as heavily obfuscated, dynamically creating a downloader and an LNK dropper during execution. The downloader tries to contact a remote server every 3 minutes to fetch additional malware, while the LNK dropper spreads through local and network drives every 9 minutes.
The malware replaces existing .pdf, .docx, and .xlsx files with deceptive shortcuts, hiding the originals. When launched, these shortcuts run PteroLNK instead.
"These scripts are designed to be flexible, allowing attackers to easily change parameters like file names, persistence mechanisms, and detection logic," HarfangLab explained.
GammaSteel Stealer
The Symantec Threat Hunter team revealed that the downloader and the LNK dropper are used to distribute an updated version of the GammaSteel stealer. The two components involved are:
- NTUSER.DAT.TMContainer00000000000000000001.regtrans-ms (Downloader)
- NTUSER.DAT.TMContainer00000000000000000002.regtrans-ms (LNK dropper)
Key Takeaways
"Gamaredon is a critical part of Russia's cyber operations, especially in the war with Ukraine," Symantec stated. "Their effectiveness isn't about technical wizardry, but about adapting their tactics."
They use spearphishing, heavily obfuscated custom malware, and redundant C2 infrastructure. They prioritize operational impact over stealth, even using domains publicly linked to their past operations.