PoisonSeed Campaign Drains Crypto Wallets Via CRM Breach
A sophisticated new campaign, dubbed PoisonSeed, is targeting cryptocurrency users by exploiting vulnerabilities in customer relationship management (CRM) systems. Attackers are using stolen CRM credentials and bulk email services to distribute spam containing compromised crypto seed phrases, hoping to gain access to and empty victims' digital wallets.

A sneaky new campaign, dubbed PoisonSeed, is making waves in the crypto world. Hackers are breaking into customer relationship management (CRM) tools and bulk email services to send spam containing cryptocurrency seed phrases. Their goal? To empty your digital wallet.
Silent Push, a cybersecurity firm, broke down the attack, explaining, "Recipients of the bulk spam are targeted with a cryptocurrency seed phrase poisoning attack. PoisonSeed provides security seed phrases to get potential victims to copy and paste them into new cryptocurrency wallets, setting them up for a future compromise." You can read their full analysis here.
Who's in the crosshairs? Apparently, everyone from big companies to individuals, even if they aren't heavily involved in the crypto scene. Big names like Coinbase, Ledger, Mailchimp, SendGrid, Hubspot, Mailgun, and Zoho are all potential targets.
Interestingly, researchers believe this campaign is separate from groups like Scattered Spider and CryptoChameleon, even though they operate within the same cybercrime network, "The Com." Security experts Troy Hunt and Bleeping Computer flagged similar activity last month.
Here's how it works: the attackers create fake login pages that look just like the real deal for popular CRM and email marketing platforms. They trick victims into entering their usernames and passwords. Once they have that info, they create an API key, ensuring they maintain access even if the victim changes their password.
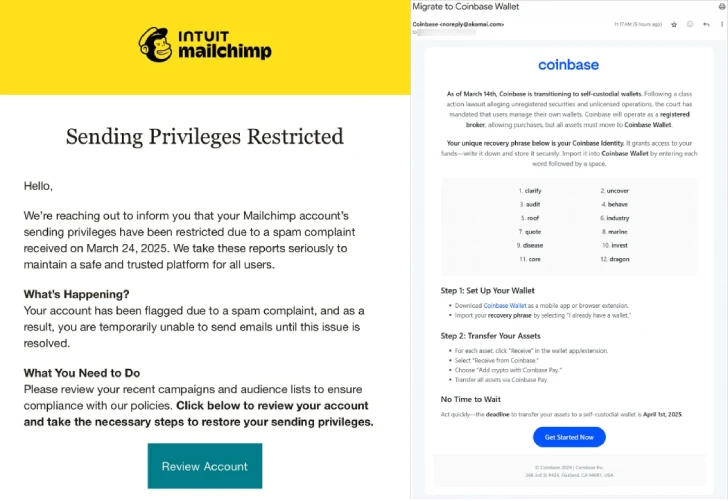
Next, they download mailing lists (likely using some automated tool) and start blasting out spam from the compromised accounts. These emails often instruct users to set up a new Coinbase Wallet using the seed phrase included in the email.
The ultimate goal is simple: use that recovery phrase to take control of the victim's wallets and steal their funds. The connection to Scattered Spider and CryptoChameleon comes from the use of a specific domain ("mailchimp-sso[.]com") previously linked to Scattered Spider, as well as CryptoChameleon's history of targeting Coinbase and Ledger users.
However, the phishing kit used in the PoisonSeed campaign doesn't resemble those used by the other two groups. This suggests it's either a brand-new kit from CryptoChameleon or a completely different threat actor employing similar tactics.
In related news, a Russian-speaking group is using phishing pages hosted on Cloudflare's Pages.Dev and Workers.Dev to spread malware capable of remotely controlling infected Windows machines. An earlier version of this campaign also distributed the StealC information stealer.
Hunt.io reports that "This recent campaign leverages Cloudflare-branded phishing pages themed around DMCA (Digital Millennium Copyright Act) takedown notices served across multiple domains." You can read more about their research here.
"The lure abuses the ms-search protocol to download a malicious LNK file disguised as a PDF via a double extension. Once executed, the malware checks in with an attacker-operated Telegram bot-sending the victim's IP address-before transitioning to Pyramid C2 to control the infected host."