Play Praetor Campaign Explodes CTM360 Reveals Massive Expansion
The Play Praetor campaign, initially flagged by CTM360 for targeting banks via roughly 6,000 URLs, has ballooned dramatically. New research indicates the attack now leverages over 16,000 URLs and multiple variations, suggesting a significant escalation. CTM360's investigation is ongoing, with further discoveries anticipated.

The PlayPraetor Campaign Quick Overview
Security firm CTM360 has uncovered a significantly larger operation behind the PlayPraetor campaign than initially thought. What started with over 6,000 URLs linked to a specific banking attack has ballooned to over 16,000, with multiple variations popping up. And the investigation is still ongoing, so expect more to come!
Just like before, these PlayPraetor copycats are designed to look like legitimate app listings. They trick users into downloading malicious Android apps or handing over their personal information. These weren't just isolated incidents; further digging revealed a well-coordinated global campaign that's seriously messing with the Google Play Store's trustworthiness.
How the Threat is Evolving
Want a closer look? This report builds on previous research, shedding light on five *new* PlayPraetor variants. These new versions show how the attackers are getting smarter with their techniques, how they're spreading the malware, and the social engineering tricks they're using. PlayPraetor's constant evolution proves how adaptable and persistent it is in targeting the Android world.
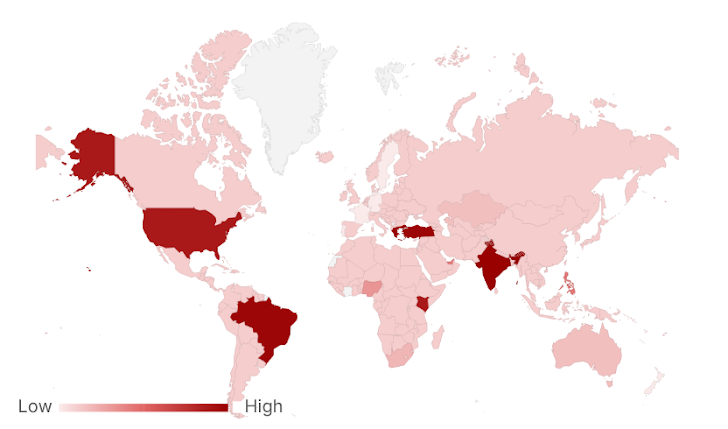
Targeting and Regional Focus: Who's Getting Hit?
Besides the original PlayPraetor Banking Trojan, we now have five more: Phish, RAT, PWA, Phantom, and Veil. These bad apps are spread through fake websites that look almost identical to the Google Play Store. While they share some nasty behaviors, each one has its own unique features, tailored to specific regions and targets. Think Philippines, India, South Africa, and other global markets.
These variants use a mix of tricks, from stealing login info and gaining remote access to installing dodgy web apps, abusing Android's accessibility features, and using sneaky tactics to hide their malicious actions behind trusted brands.
What's the Goal? Attack Objectives and Industry Focus
Even though each variant has its own quirks and targets different regions, they all have one thing in common: a focus on the financial sector. The criminals behind these variants are after banking logins, credit card details, digital wallet access, and sometimes even making fraudulent transactions by moving money to dummy accounts. This points to a well-organized operation with a clear goal: making money.
A Quick Look at the Variants
These five new variants – Phish, RAT, PWA, Phantom, and Veil – are currently being investigated. Some have confirmed detection numbers, while others are still being analyzed. Here's a table summarizing what we know so far, along with a more detailed technical breakdown.
| Variant Name | Functionality | Description | Target Industry | Detected Cases (Approx.) |
| PlayPraetor PWA | Deceptive Progressive Web App | Installs a fake PWA that mimics legitimate apps, creates shortcuts on the home screen, and triggers persistent push notifications to lure interaction. | Technology Industry, Financial Industry, Gaming Industry, Gambling Industry, e-commerce Industry | 5400+ |
| PlayPraetor Phish | WebView phishing | A WebView-based app that launches a phishing webpage to steal user credentials. | Financial, Telecommunication, Fast Food Industry | 1400+ |
| PlayPraetor Phantom | Stealthy Persistence & Command Execution | Exploits Android accessibility services for persistent control. Runs silently, exfiltrates data, hides its icon, blocks uninstallation, and poses as a system update. | Financial Industry, Gambling Industry, Technology Industry | These variants are currently under investigation to determine their exact identities. |
| PlayPraetor RAT | Remote Access Trojan | Grants attackers full remote control of the infected device, enabling surveillance, data theft, and manipulation. | Financial Industry | |
| PlayPraetor Veil | Regional & Invitation-based Phishing | Disguises itself using legitimate branding, restricts access via invite codes, and imposes regional limitations to avoid detection and increase trust among local users. | Financial Industry, Energy Industry |
Where are These Attacks Happening?
CTM360's data shows that while PlayPraetor is a global problem, some versions are more widespread than others. The Phantom-WW variant, for example, is designed to hit anyone, anywhere. By mimicking a popular global app, the attackers can cast a wider net and trick more people.
The PWA variant is the most common, popping up across South America, Europe, Oceania, Central Asia, South Asia, and parts of Africa. It's definitely the most widespread variant in the PlayPraetor campaign.
Other variants are more targeted. The Phish variant is also found in multiple regions, but not as heavily as PWA. The RAT variant is mostly found in South Africa, suggesting a specific focus. And the Veil variant is mainly seen in the United States and a few African nations, indicating a more targeted strategy.
Staying Safe: How to Protect Yourself
So, how do you avoid becoming a victim of PlayPraetor and similar scams?
- ✅ Stick to official sources: Only download apps from the official Google Play Store or Apple App Store.
- ✅ Do your homework: Check out the app developer and read reviews before installing anything.
- ✅ Be stingy with permissions: Avoid granting unnecessary permissions, especially Accessibility Services.
- ✅ Use security software: Employ mobile security solutions to detect and block malware-infected apps.
- ✅ Stay informed: Keep up with the latest threats by reading cybersecurity reports.
Want to dive deeper? Read the full report here.