Paper Werewolf APT Hunts Russian Targets with Stealthy PowerModul Malware
A hacking group dubbed Paper Werewolf is exclusively targeting Russian organizations with a newly discovered implant called PowerModul, suggesting a focused and deliberate espionage campaign.

The cybercrime group known as Paper Werewolf is at it again, this time targeting Russian organizations with a brand-new piece of malware called PowerModul. Seems like no one is safe these days!
According to a recent report from Kaspersky , these attacks took place between July and December 2024, hitting companies in media, telecom, construction, government, and even the energy sector. Talk about a wide net!
So, who is Paper Werewolf? Also known as GOFFEE, this group has been active since at least 2022, launching at least seven different campaigns, according to BI.ZONE . Their targets usually include government agencies, energy providers, financial institutions, media outlets, and other juicy targets.
What's even more concerning is that Paper Werewolf isn't just after data. These guys are also known to disrupt operations by changing employee account passwords during their intrusions. That’s going beyond just stealing information!
How the Attacks Unfold
The initial attack usually starts with a phishing email containing a seemingly harmless document. But here’s the trick – the document contains malicious macros. If you open the document and enable those macros (don't do it!), you're basically opening the door for a PowerShell-based remote access trojan called PowerRAT.
This PowerRAT is just the beginning. It's designed to deliver even more malicious code, often a customized version of the Mythic framework agent called PowerTaskel and QwakMyAgent. They also use a nasty IIS module called Owowa to steal Microsoft Outlook credentials.
Kaspersky's report details how the latest attacks begin with a malicious RAR archive attached to an email. This archive contains an executable file disguised as a PDF or Word document using a clever double extension trick (like *.pdf.exe). When you run the executable, it downloads a fake PDF or Word file to show you, while secretly installing malware in the background.
According to Kaspersky, "The file itself is a Windows system file (explorer.exe or xpsrchvw.exe), with part of its code patched with a malicious shellcode. The shellcode is similar to what we saw in earlier attacks, but in addition contains an obfuscated Mythic agent, which immediately begins communicating with the command-and-control (C2) server."
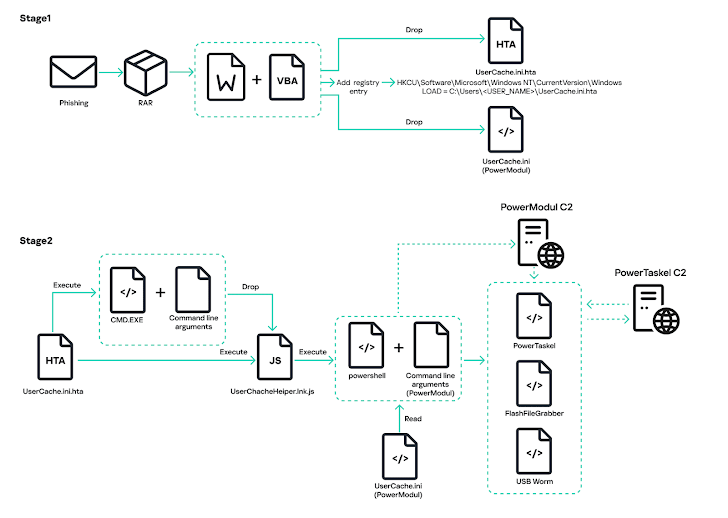
Another attack method involves a RAR archive containing a Microsoft Office document with a macro. This macro acts as a "dropper," deploying and launching PowerModul, a PowerShell script that can receive and execute more PowerShell scripts from the attackers' command-and-control server.
This PowerModul backdoor has been in use since early 2024, initially used to download and run PowerTaskel on compromised systems. Here are some of the payloads it drops:
- FlashFileGrabber: Steals files from USB drives and sends them to the C2 server.
- FlashFileGrabberOffline: A variant that searches USB drives for specific file types, copies them to a temporary folder, and then exfiltrates them.
- USB Worm: Infects USB drives with a copy of PowerModul to spread the infection further.
PowerTaskel works similarly to PowerModul, running PowerShell scripts sent by the C2 server. It can also gather information about the victim's system and execute commands. Plus, it can even try to gain higher privileges using the PsExec utility.
In one case, PowerTaskel received a script with a FolderFileGrabber component, which not only steals files from USB drives but also grabs files from network shares using the SMB protocol.
"For the first time, they employed Word documents with malicious VBA scripts for initial infection," Kaspersky noted. "Recently, we have observed that GOFFEE is increasingly abandoning the use of PowerTaskel in favor of the binary Mythic agent during lateral movement."
Sapphire Werewolf Joins the Fray
Adding to the chaos, BI.ZONE attributed another group, Sapphire Werewolf, to a phishing campaign spreading an updated version of the Amethyst Stealer.
This stealer is designed to grab "credentials from Telegram and various browsers, including Chrome, Opera, Yandex, Brave, Orbitum, Atom, Kometa, and Edge Chromium, as well as FileZilla and SSH configuration files," according to BI.ZONE. It can also steal documents, including those stored on USB drives.