North Korean Lazarus Group Targets South Korean Companies Exploiting Software Vulnerabilities
The notorious North Korean hacking group Lazarus is suspected of breaching at least six South Korean organizations in a campaign security researchers are calling Operation SyncHole. The attacks leveraged vulnerabilities in software from Cross EX and Innorix, and employed the ThreatNeedle malware to gain access and move laterally within the compromised networks.

The notorious North Korean hacking group, Lazarus Group, is at it again. This time, they've set their sights on South Korea in a campaign dubbed "Operation SyncHole," targeting at least six organizations.
Kaspersky's latest report reveals that the attacks are focused on South Korea's software, IT, financial, semiconductor manufacturing, and telecommunications sectors. The first signs of trouble surfaced back in November 2024.
Watering Hole Attacks and Zero-Day Exploits
According to security researchers Sojun Ryu and Vasily Berdnikov, the campaign uses a clever mix of "watering hole" tactics and exploiting vulnerabilities in South Korean software. They noted the attackers even used a one-day vulnerability in Innorix Agent for lateral movement within the compromised networks.
The attacks are paving the way for familiar Lazarus Group tools, including:
Cross EX Vulnerability: A Key to Success
What's making these attacks so effective? It seems the Lazarus Group is exploiting a security hole in Cross EX, a popular software used in South Korea for online banking and government websites. This software is designed to provide security features like anti-keylogging and digital signature support.
Kaspersky points out that the Lazarus Group clearly understands the South Korean landscape, combining software vulnerabilities with watering hole attacks to maximize their impact.
Interestingly, the exploitation of the Innorix Agent vulnerability for lateral movement isn't new. The Andariel sub-cluster of Lazarus Group has used similar tactics in the past, deploying malware like Volgmer and Andardoor.
How the Attack Unfolds
The initial attack starts with a watering hole strategy. Victims visiting compromised South Korean online media sites are filtered using a server-side script. If they meet certain criteria, they're redirected to a malicious domain that serves up the malware.
"We believe the redirected site likely executes a malicious script, targeting a potential flaw in Cross EX," the researchers explained. "This script then executes the legitimate SyncHost.exe and injects a shellcode that loads a variant of ThreatNeedle."
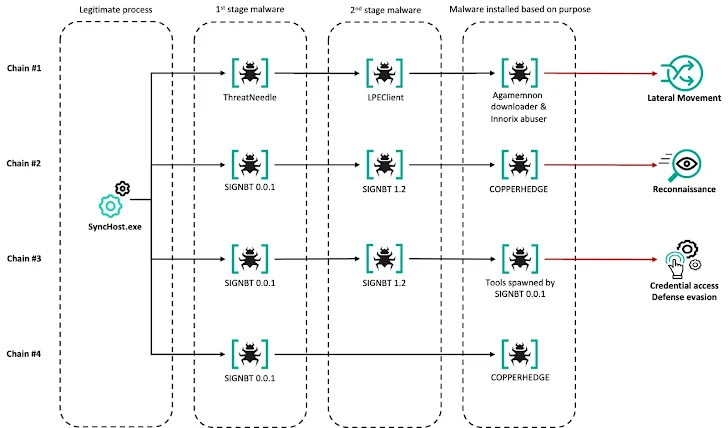
The infection occurs in two phases. First, ThreatNeedle and wAgent are deployed. Later, SIGNBT and COPPERHEDGE are used to establish persistence, gather information, and steal credentials.
Other malware families, such as LPEClient (for victim profiling) and Agamemnon (a downloader), are also used. Agamemnon retrieves additional payloads from the command-and-control server, using the "Hell's Gate" technique to evade security measures.
Innorix Agent Zero-Day Patched
One of the payloads downloaded by Agamemnon exploits a vulnerability in the Innorix Agent file transfer tool, enabling lateral movement. Kaspersky discovered another zero-day vulnerability in Innorix Agent that has since been patched.
What's Next?
Kaspersky warns that the Lazarus Group's focus on South Korean supply chains is likely to continue. They're also actively working to evade detection by developing new malware and improving existing tools. This includes enhancing communication with command-and-control servers and modifying their command structures.