North Korean Hackers Use Crypto Job Scams to Deploy Malware
A North Korean hacking group is disguising itself as legitimate cryptocurrency firms to lure unsuspecting job seekers into downloading malware. The group, known for its "Contagious Interview" tactics, establishes shell companies to distribute malicious software during fake hiring processes.

Remember the Contagious Interview? Well, North Korea-linked hackers are at it again. This time, they're setting up fake companies to distribute malware through bogus job opportunities.
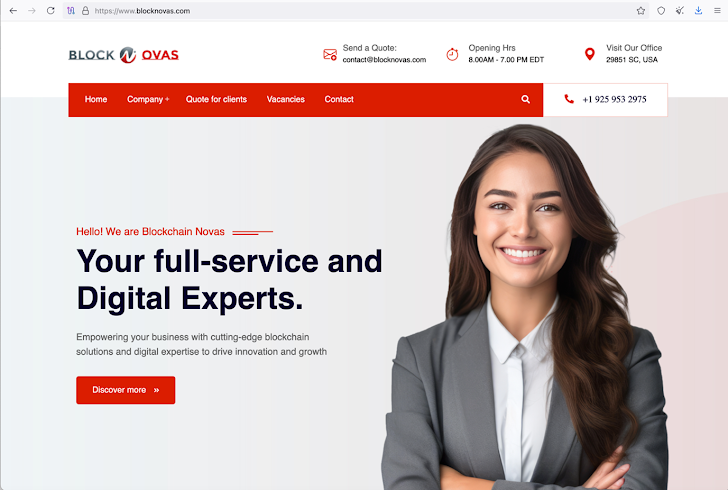
Cybersecurity firm Silent Push uncovered that these hackers are using three shell companies – BlockNovas LLC (blocknovas[.]com), Angeloper Agency (angeloper[.]com), and SoftGlide LLC (softglide[.]co) – to spread malware under the guise of "job interview lures." You can read their full analysis here.
So what kind of malware are we talking about? According to Silent Push, they're distributing three familiar families: BeaverTail, InvisibleFerret, and OtterCookie.
The "Contagious Interview" is just one of many social engineering tactics North Korea uses. They try to trick people into downloading malware disguised as coding assignments or browser fixes needed when turning on a camera during an interview.
The cybersecurity world is tracking this activity under a bunch of different names: CL-STA-0240, DeceptiveDevelopment, DEV#POPPER, Famous Chollima, UNC5342, and Void Dokkaebi.
Using these front companies to spread malware, combined with fake accounts on social media platforms like Facebook, LinkedIn, and X, is a serious escalation. These hackers have been known to use job boards to lure victims, but this is a new level of sophistication.
"BlockNovas claims to have 14 employees, but many of them appear to be fake," Silent Push notes. "Their 'About Us' page on the Wayback Machine claimed they've been around for '12+ years' – that's way longer than they've actually been registered."
The attacks often start with a JavaScript stealer and loader called BeaverTail. This then drops a Python backdoor called InvisibleFerret, which allows them to stay persistent on Windows, Linux, and macOS systems. Some attacks also involve OtterCookie, delivered through the same JavaScript payload as BeaverTail.
BlockNovas has even used video assessments to distribute FROSTYFERRET and GolangGhost using "ClickFix" lures. Sekoia, tracking this under the name "ClickFake Interview," detailed this tactic earlier this month.
BeaverTail connects to an external server ("lianxinxiao[.]com") to get instructions and download InvisibleFerret. It can collect system information, launch a reverse shell, steal browser data and files, and even install AnyDesk remote access software.
Further digging into the malicious infrastructure revealed a "Status Dashboard" hosted on a BlockNovas subdomain. This dashboard was used to monitor four domains: lianxinxiao[.]com, angeloperonline[.]online, and softglide[.]co.
They also found that mail.blocknovas[.]com was hosting Hashtopolis, an open-source password cracking system. These fake recruitment drives have even led to developers having their MetaMask wallets compromised as far back as September 2024.
And there's more! The hackers appear to be hosting a tool called Kryptoneer on attisscmo[.]com, which can connect to crypto wallets like Suiet Wallet, Ethos Wallet, and Sui Wallet.
Silent Push suggests that North Korea may be specifically targeting the Sui blockchain, or using this domain as a "crypto project" example during job applications.
A report by Trend Micro also revealed that BlockNovas advertised a senior software engineer position on LinkedIn in December 2024, specifically targeting Ukrainian IT professionals.
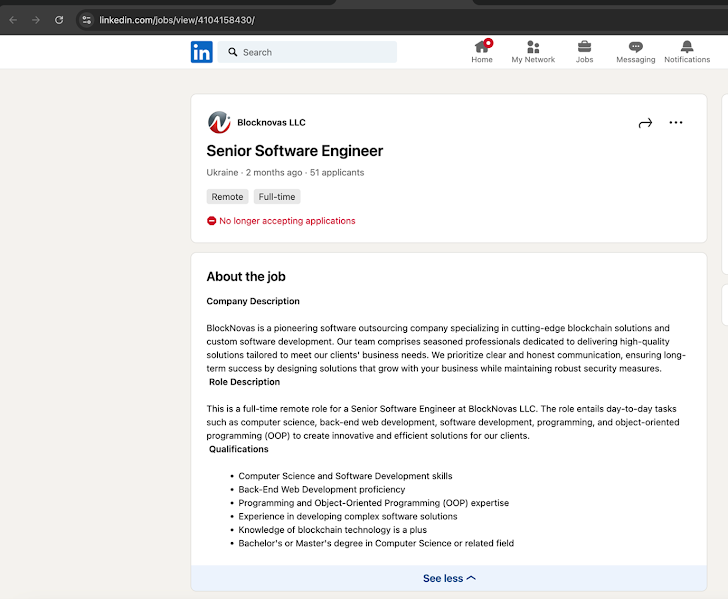
As of April 23, 2025, the FBI seized the BlockNovas domain as part of a crackdown on North Korean cyber actors. They were using it to "deceive individuals with fake job postings and distribute malware."
To hide their tracks, the hackers use services like Astrill VPN and residential proxies. They even use AI-powered tools like Remaker to create realistic profile pictures.
Silent Push also identified five Russian IP ranges used in the campaign, hidden behind VPNs, proxies, and RDP layers.
Security researchers Feike Hacquebord and Stephen Hilt from Trend Micro explained that these Russian IP addresses are connected to two companies in Khasan and Khabarovsk.
"Khasan is just a mile from the North Korea-Russia border, and Khabarovsk is known for its economic and cultural ties with North Korea."
This "Contagious Interview" is only one side of the coin. The other is the "Wagemole" threat, where hackers create fake personas using AI to get hired remotely at major companies. You can read more about Wagemole here.
These efforts are designed to steal data and generate income for North Korea by funneling portions of the salaries back to the DPRK.
The use of GenAI-based tools is optimizing every stage of the job application process, from creating fake resumes to acing interviews, helping North Korean nationals land remote positions.