North Korean Hackers Target Developers with Fake Packages on npm
A North Korean hacking group known for the "Contagious Interview" campaign is expanding its reach, now targeting software developers using malicious packages uploaded to the npm registry. These packages deliver the BeaverTail malware and a new remote access trojan loader, putting developers and their projects at risk.

Remember the Contagious Interview campaign? Well, the North Korean hackers behind it are now targeting the npm ecosystem, pushing out more malicious packages that install the BeaverTail malware and a brand-new remote access trojan (RAT) loader. It seems like they're not slowing down!
According to Socket security researcher Kirill Boychenko, these new attacks use clever tricks to hide their code. "These latest samples employ hexadecimal string encoding to evade automated detection systems and manual code audits, signaling a variation in the threat actors' obfuscation techniques," Boychenko said. Basically, they're making it harder for security tools and people to spot the bad stuff.
So, what packages should you watch out for? These ones were downloaded over 5,600 times before they were removed:
- empty-array-validator
- twitterapis
- dev-debugger-vite
- snore-log
- core-pino
- events-utils
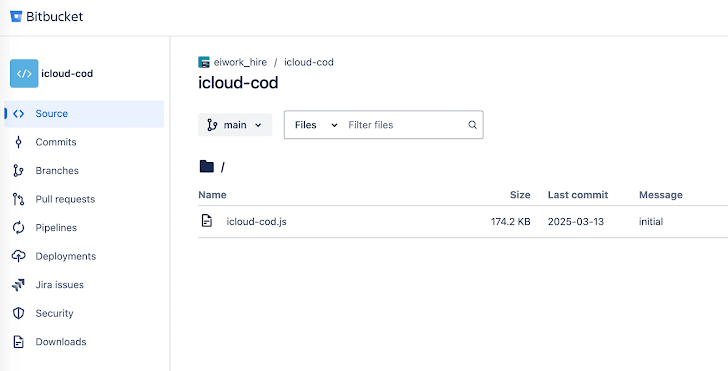
- icloud-cod
- cln-logger
- node-clog
- consolidate-log
- consolidate-logger
Just last month, six npm packages were caught spreading BeaverTail, a JavaScript stealer that can also deliver a Python backdoor called InvisibleFerret. It's a nasty piece of work.
The overall goal? To sneak into developer systems by pretending to be recruiters. Once inside, they steal data, grab cash, and try to maintain long-term access.
These malicious npm libraries pose as helpful tools and debuggers. One of them, dev-debugger-vite, even used a command-and-control (C2) address previously linked to the Lazarus Group in a campaign called Phantom Circuit. Talk about a red flag!
Here's a twist: some of these packages, like events-utils and icloud-cod, are hosted on Bitbucket instead of GitHub. Plus, the icloud-cod package was found in a directory called "eiwork_hire," which is another hint that they're using fake job interviews to trick people.
Analyzing the code of cln-logger, node-clog, consolidate-log, and consolidate-logger revealed slight differences, suggesting the attackers are launching multiple versions of the malware to boost their chances of success.
No matter the changes, the malicious code in these packages acts as a remote access trojan (RAT) loader. It grabs a second-stage payload from a remote server and gets to work.
"The Contagious Interview threat actors continue to create new npm accounts and deploy malicious code across platforms like the npm registry, GitHub, and Bitbucket, demonstrating their persistence and showing no signs of slowing down," Boychenko warned.
He added, "The advanced persistent threat (APT) group is diversifying its tactics — publishing new malware under fresh aliases, hosting payloads in both GitHub and Bitbucket repositories, and reusing core components like BeaverTail and InvisibleFerret alongside newly observed RAT/loader variant."
BeaverTail Drops Tropidoor
And there's more! South Korean cybersecurity firm AhnLab discovered a phishing campaign using recruitment themes. This campaign delivers BeaverTail, which then deploys a new Windows backdoor called Tropidoor. It looks like developers in South Korea are being actively targeted.
The phishing email, claiming to be from a company called AutoSquare, includes a link to a Bitbucket project. The email urges recipients to clone the project and review the code.
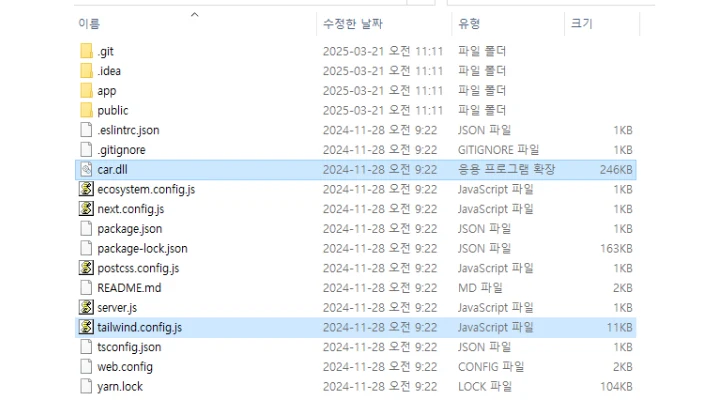
The application turns out to be a malicious npm library containing BeaverTail ("tailwind.config.js") and a DLL downloader ("car.dll"). The JavaScript stealer and loader then launches the DLL.
Tropidoor is a sneaky backdoor that "operates in memory through the downloader." It connects to a C2 server for instructions, allowing it to steal files, gather system information, run and stop processes, take screenshots, and even wipe files.
Interestingly, Tropidoor directly uses Windows commands like schtasks, ping, and reg. This tactic was also seen in another Lazarus Group malware called LightlessCan, which followed in the footsteps of BLINDINGCAN.
"Users should be cautious not only with email attachments but also with executable files from unknown sources," AhnLab warned. Stay safe out there!