North Korean Hackers Leverage Old Windows Flaw in Attacks Targeting South Korea and Japan
A notorious North Korean hacking group, Kimsuky, is back in action, leveraging a well-known but unpatched vulnerability in Microsoft's Remote Desktop Services (RDP) to infiltrate systems in South Korea and Japan. Cybersecurity experts warn that the group is exploiting the 'BlueKeep' flaw, despite Microsoft releasing a patch years ago, highlighting the critical need for organizations to keep their systems up to date.
Security researchers are sounding the alarm about a new hacking campaign linked to Kimsuky, a notorious North Korean state-sponsored group. This time, they're exploiting an old but still potent vulnerability in Microsoft's Remote Desktop Services (RDS) to break into systems.
AhnLab, a South Korean cybersecurity firm, has dubbed this activity "Larva-24005."
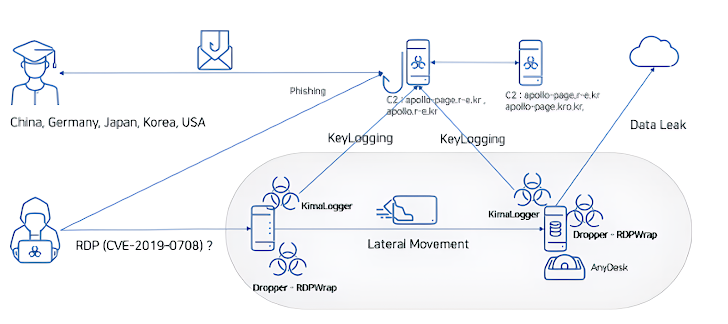
According to AhnLab, "In some systems, initial access was gained through exploiting the RDP vulnerability (BlueKeep, CVE-2019-0708)." They also noted, "While an RDP vulnerability scanner was found in the compromised system, there is no evidence of its actual use." You can read their full report here.
What's BlueKeep and Why Should You Care?
CVE-2019-0708, or BlueKeep as it's commonly known, is a serious flaw in RDS. It's rated as critical (CVSS score: 9.8) because it's "wormable," meaning it can spread rapidly from one vulnerable computer to another. This bug could let hackers remotely run code, install software, steal data, and even create new administrator accounts. Think of it as giving them the keys to the kingdom.
To exploit BlueKeep, attackers need to send a specially crafted request to a vulnerable system's RDS via RDP. Microsoft patched this back in May 2019, so if you've kept your systems updated, you should be safe. But sadly, not everyone does...
Phishing is Still a Favorite Tactic
BlueKeep isn't the only trick up Kimsuky's sleeve. They're also using phishing emails containing files that exploit another old vulnerability, this time in Microsoft Equation Editor (CVE-2017-11882, CVSS score: 7.8). It just goes to show that even old vulnerabilities can be effective when people aren't careful.
Once they get in, the hackers install a piece of malware called MySpy and a tool called RDPWrap, which helps them enable RDP access. MySpy is designed to collect system information, giving them a better understanding of their victim's network.
Keyloggers and Targeted Sectors
The final step in the attack involves deploying keyloggers like KimaLogger and RandomQuery to steal passwords and other sensitive information.
This campaign appears to be targeting organizations in South Korea and Japan, particularly those in the software, energy, and financial sectors. However, Kimsuky has a wider reach, with past targets including organizations in the United States, China, Germany, and many other countries.