Nation-State Hackers Exploit ClickFix in Sophisticated Malware Attacks
Elite hacking teams with suspected ties to Iran, North Korea, and Russia are using a clever social engineering trick called ClickFix to sneak malware onto targeted systems. These campaigns, observed between late 2024 and early 2025, highlight the growing sophistication and coordinated efforts of state-backed cyber adversaries.

Looks like even nation-state hackers are adopting new tricks. Security researchers have spotted multiple government-backed groups from Iran, North Korea, and Russia using a social engineering tactic called "ClickFix" to spread malware. This trend was observed over a three-month period, starting in late 2024 and continuing into early 2025.
These phishing campaigns have been linked to groups known as TA427 (aka Kimsuky), TA450 (aka MuddyWater), UNK_RemoteRogue, and TA422 (aka APT28). So, pretty serious players.
While ClickFix was initially a favorite of cybercrime gangs, its effectiveness is clearly attracting the attention of these more sophisticated, nation-state actors.
According to a recent report from Proofpoint, "The incorporation of ClickFix is not revolutionizing the campaigns carried out by TA427, TA450, UNK_RemoteRogue, and TA422 but instead is replacing the installation and execution stages in existing infection chains." You can read the full report here.
So, what exactly is ClickFix? Essentially, it's a deceptive technique that tricks users into infecting themselves. Victims are guided through a series of steps – copying, pasting, and running malicious commands – under the guise of fixing a problem, completing a CAPTCHA, or registering a device. Tricky, right?
Proofpoint noted that Kimsuky first used ClickFix in January and February of 2025, targeting a small number of think tanks.
"TA427 made initial contact with the target through a meeting request from a spoofed sender delivered to traditional TA427 targets working on North Korean affairs," the Proofpoint team explained.
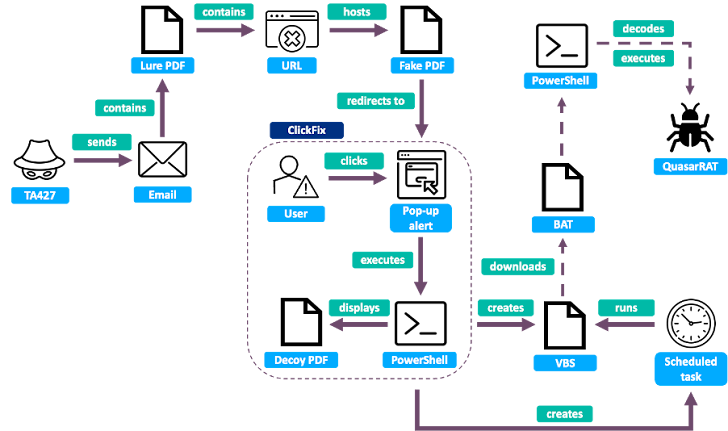
TA427 ClickFix infection chain
According to the researchers, "After a brief conversation to engage the target and build trust, as is often seen in TA427 activity, the attackers directed the target to an attacker-controlled site where they convinced the target to run a PowerShell command."
This attack chain then leads to the deployment of Quasar RAT, an open-source remote access trojan.
In one instance, the email appeared to be from a Japanese diplomat, requesting a meeting with the Japanese ambassador. The attackers then sent a malicious PDF containing a link to a document with questions for the meeting.
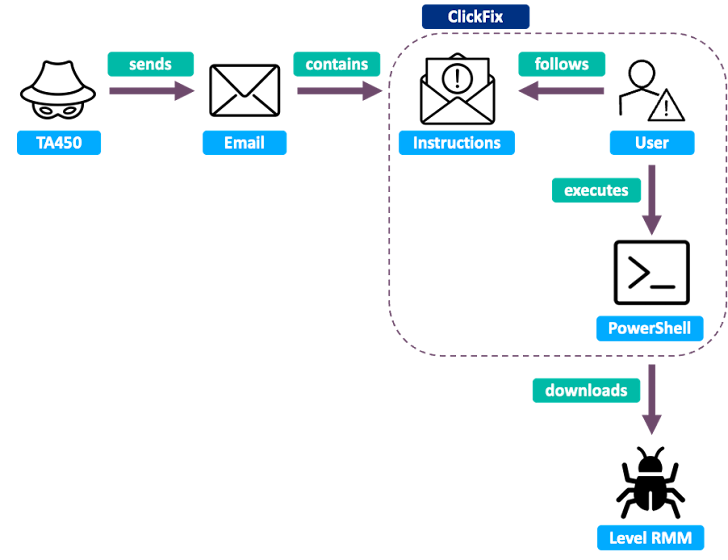
TA450 ClickFix infection chain
Clicking that link took the victim to a fake Japanese Embassy website. The site then prompted them to "register" their device by copying and pasting a command into the Windows Run dialog, which downloaded the questionnaire.
Proofpoint explained, "The ClickFix PowerShell command fetches and executes a second remotely hosted PowerShell command, which displayed the decoy PDF referenced earlier in the chain (Questionnaire.pdf) to the user. The document claimed to be from the Ministry of Foreign Affairs in Japan and contained questions regarding nuclear proliferation and policy in Northeast Asia."
That second PowerShell script creates a Visual Basic Script that runs every 19 minutes via a scheduled task. This then downloads two batch scripts that create, decode, and execute the Quasar RAT payload. Microsoft previously documented a similar attack chain in February 2025.
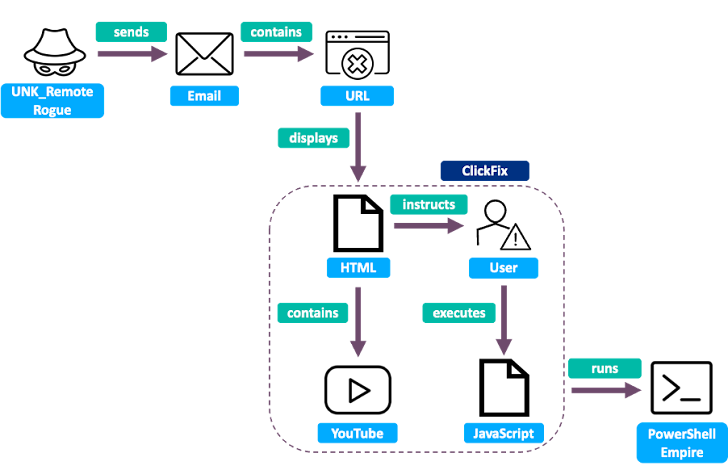
UNK_RemoteRogue ClickFix infection chain
MuddyWater, an Iranian group, is also using ClickFix, but with a twist. They're leveraging legitimate remote monitoring and management (RMM) software, like Level, to maintain persistent access to compromised systems.
Their phishing emails, sent around Microsoft's Patch Tuesday in November 2024, posed as security updates and instructed recipients to use ClickFix-style commands to fix a supposed vulnerability.
Proofpoint stated, "The attackers deployed the ClickFix technique by persuading the target to first run PowerShell with administrator privileges, then copy and run a command contained in the email body."
This command installs the RMM software. Then, TA450 uses the RMM tool for espionage and data exfiltration.