Fast Flux Technique Shields Cybercriminals From Detection, Warns CISA and FBI
A coalition of cybersecurity agencies, including those from the US, Australia, Canada, and New Zealand, is raising alarms about "fast flux," a technique that allows cybercriminals to build incredibly resilient malware, command-and-control, and phishing networks by constantly shifting their online infrastructure and evading detection.

Ever heard of "fast flux"? It's a sneaky technique used by cybercriminals to hide their tracks, and now cybersecurity agencies are sounding the alarm. Agencies from Australia, Canada, New Zealand, and the U.S. have jointly warned about the risks of this tactic, which helps malicious actors keep their command-and-control (C2) channels under wraps.
Think of it like this: imagine trying to catch a fly that's constantly buzzing around, never landing in the same spot for long. That's essentially what fast flux does. As the agencies put it, it "obfuscates the locations of malicious servers through rapidly changing Domain Name System (DNS) records." It exploits weaknesses in network defenses, making it tough to track and block malicious activity.
This warning comes from a coalition of top security watchdogs: CISA, NSA, FBI, the Australian Signals Directorate's Australian Cyber Security Centre, the Canadian Centre for Cyber Security, and New Zealand's National Cyber Security Centre.
So, who's using fast flux? It's become a favorite among several hacking groups, including those tied to Gamaredon, CryptoChameleon, and Raspberry Robin. They're using it to make their infrastructure harder to detect and take down.
The basic idea is to use a bunch of different IP addresses and rotate them really quickly, all while pointing to the same malicious domain. It's like a game of whack-a-mole for cybersecurity professionals. This technique first surfaced in 2007, thanks to the Honeynet Project.
There are two main types of fast flux:
- Single flux: A single domain name is linked to many IP addresses.
- Double flux: Not only do the IP addresses change, but the DNS name servers responsible for resolving the domain also change frequently. This adds an extra layer of protection for the bad guys.
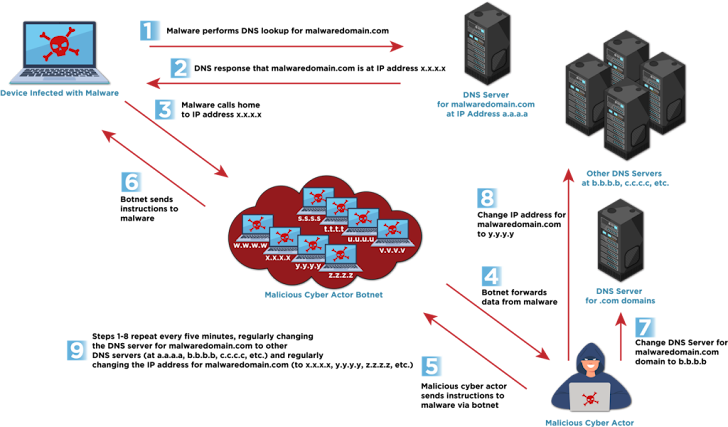
As Palo Alto Networks Unit 42 explained, "A fast flux network is 'fast' because, using DNS, it quickly rotates through many bots, using each one for only a short time to make IP-based denylisting and takedown efforts difficult."
The agencies are calling fast flux a national security threat because it helps attackers hide malicious servers and build resilient C2 infrastructure that can withstand takedowns.
Beyond Command and Control
Fast flux isn't just about C2 communications. It also helps attackers host phishing websites and distribute malware. It's a versatile tool in their arsenal.
How to Defend Against Fast Flux
So, what can you do to protect yourself? Here are a few recommendations:
- Block suspicious IP addresses.
- Sinkhole malicious domains.
- Filter traffic to and from domains or IP addresses with bad reputations.
- Implement better monitoring systems.
- Train employees to spot phishing attempts.
"Fast flux represents a persistent threat to network security," the agencies warned. "By implementing robust detection and mitigation strategies, organizations can significantly reduce their risk of compromise."