Fake Job Offers Used to Spread Iranian Malware in Israel
An Iranian hacking group, tracked as UNC2428, is suspected of using a sophisticated social engineering campaign targeting individuals in Israel. In October 2024, researchers observed the group distributing a backdoor known as MURKYTOUR disguised as legitimate job opportunities.
Ever heard of a threat actor called UNC2428? Turns out, this group, linked to Iran, was spotted using a tricky social engineering campaign to sneak malware into Israeli systems back in October 2024. The bait? Fake job opportunities.
According to Mandiant, the cybersecurity experts at Google, UNC2428 is an Iranian-aligned group focused on cyber espionage. They used a "complex chain of deception" to distribute the malware.
"UNC2428's social engineering campaign targeted individuals while posing as a recruitment opportunity from Israeli defense contractor, Rafael," Mandiant reported in their annual M-Trends report for 2025.
Here's how it worked: Interested applicants were sent to a fake website that looked just like Rafael's. They were then asked to download a tool supposedly needed to apply for the job.
This tool, cleverly named "RafaelConnect.exe," was actually malware. Once launched, it presented a fake application form, tricking users into entering their personal info and resume.
Behind the scenes, after submission, the MURKYTOUR backdoor was quietly launched, giving the attackers persistent access to the victim's computer. This was made possible by a launcher called LEAFPILE.
"Iran-nexus threat actors incorporated graphical user interfaces (GUIs) to disguise malware execution and installation as legitimate applications or software," Mandiant explained. "The addition of a GUI...can reduce suspicions from targeted individuals."
Interestingly, this campaign overlaps with activity attributed to Black Shadow, another Iranian threat actor, by the Israel National Cyber Directorate.
Black Shadow, believed to be working for the Iranian Ministry of Intelligence and Security (MOIS), is notorious for targeting various sectors in Israel, from universities to government agencies.
Mandiant points out that UNC2428 is just one of many Iranian groups targeting Israel. Another prominent example is Cyber Toufan, known for using the POKYBLIGHT wiper against Israeli users.
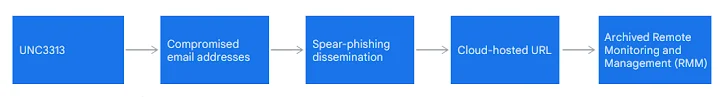
Then there's UNC3313, another Iranian group, using spear-phishing for surveillance. First spotted in February 2022, UNC3313 is thought to be linked to MuddyWater.
"The threat actor hosted malware on popular file-sharing services and embedded links within training- and webinar-themed phishing lures," Mandiant noted. They distributed the JELLYBEAN dropper and CANDYBOX backdoor through these phishing attacks.
UNC3313 frequently uses legitimate remote monitoring and management (RMM) tools – up to nine different ones! This is a common tactic of MuddyWater, helping them stay hidden and maintain remote access.
In July 2024, another suspected Iran-linked group was seen distributing the CACTUSPAL backdoor, disguised as an installer for Palo Alto Networks GlobalProtect remote access software.
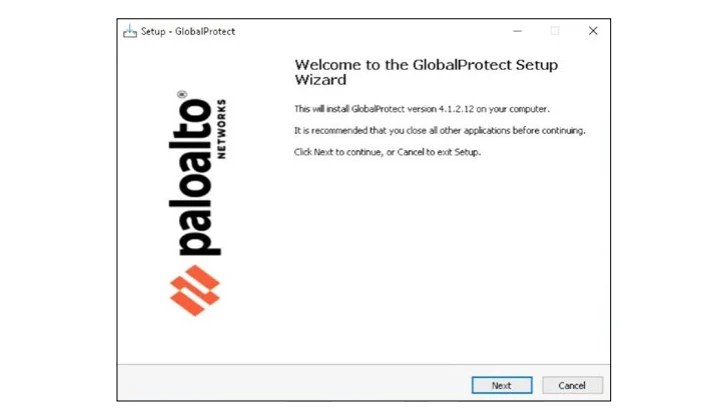
This fake installer stealthily deploys the .NET backdoor, making sure only one instance is running before connecting to a command-and-control (C2) server.
Besides using RMM tools, Iranian threat actors like UNC1549 are also using cloud infrastructure to blend in with typical enterprise services.
"Hosting C2 nodes or payloads on cloud infrastructure and using cloud-native domains reduces the scrutiny that may be applied to their operations," Mandiant explained.
You can't talk about Iranian cyber threats without mentioning APT42 (aka Charming Kitten). They're famous for their social engineering skills, building trust to steal credentials and deliver custom malware.
APT42 uses fake login pages for Google, Microsoft, and Yahoo!, using Google Sites and Dropbox to redirect targets to fake login pages or Google Meet invitations.
Overall, Mandiant identified over 20 unique malware families used by Iranian groups in the Middle East in 2024. Two backdoors, DODGYLAFFA and SPAREPRIZE, have been used by APT34 (aka OilRig) against Iraqi government organizations.
"As Iran-nexus threat actors continue to pursue cyber operations that align with the interests of the Iranian regime, they will alter their methodologies to adapt to the current security landscape," Mandiant concludes. So, stay vigilant!




