Fake App Campaign Spreads SpyNote, BadBazaar, and MOONSHINE Malware to Android and iOS
Android and iOS users are under attack from a sophisticated malware campaign using fake apps, cybersecurity experts warn. Threat actors are using newly created websites to distribute malicious software, including the notorious SpyNote Android trojan, as well as the BadBazaar and MOONSHINE malware families.

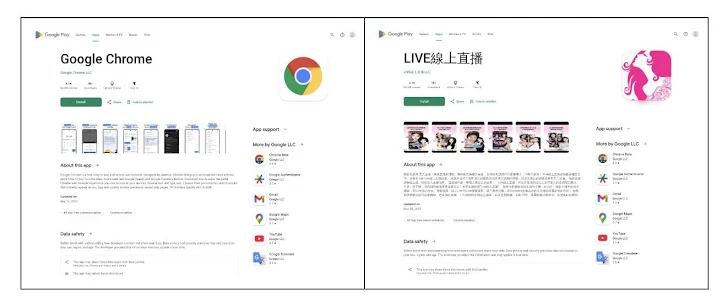
Cybersecurity researchers are reporting a new wave of attacks using the infamous SpyNote malware. Hackers are setting up fake websites, designed to look like legitimate app download pages, to trick you into installing it.
These websites are particularly sneaky, often mimicking the Google Play Store and offering downloads for popular apps like the Chrome web browser. Don't be fooled!
According to a report from the DomainTools Investigations (DTI) team, these sites use a mix of English and Chinese languages, and even include Chinese comments in the code. You can read their full report here.
So, what's the big deal about SpyNote? Well, SpyNote, also known as SpyMax, is a remote access trojan (RAT). It's been around for a while and is known for stealing sensitive data from your Android device. It does this by abusing accessibility services – features designed to help users with disabilities.
Back in May 2024, it was spread through fake antivirus websites, impersonating Avast. You can read about that here.
Interestingly, mobile security firm Zimperium has found similarities between SpyNote and another piece of malware called Gigabud. This suggests that the same group, possibly the Chinese-speaking actors known as GoldFactory, might be behind both.
And it's not just cybercriminals using SpyNote. Over the years, it's been adopted by state-sponsored hacking groups like OilAlpha and other unknown actors. Scary stuff!
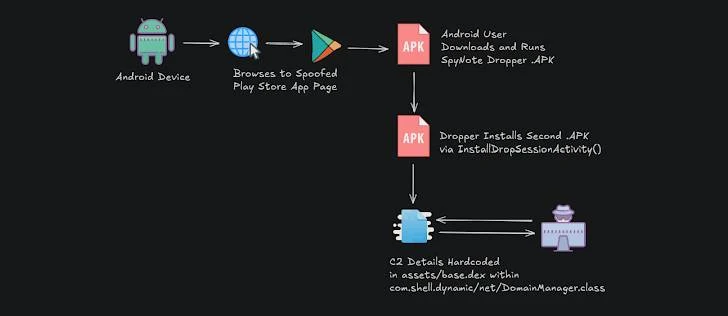
So how does this fake website trick work? The websites identified by DTI have a carousel of images. When you click on these images, a malicious APK file (the Android app package) is downloaded to your device. This APK then installs another APK, which is the SpyNote malware itself. It uses the DialogInterface.OnClickListener interface, so when you click 'install' you're actually activating the malware.
According to DTI, once installed, SpyNote "aggressively requests numerous intrusive permissions," giving it "extensive control over the compromised device."
This control allows the attackers to steal all sorts of sensitive data – SMS messages, contacts, call logs, location information, and files. It also gives them remote access to your camera and microphone, lets them manipulate calls, and even execute commands on your phone.
This news comes on the heels of a report from Lookout, which found over 4 million mobile-focused social engineering attacks in 2024. They also detected 427,000 malicious apps on enterprise devices and 1,600,000 vulnerable apps.
In fact, Lookout reports that "Over the course of the last five years, iOS users have been exposed to significantly more phishing attacks than Android users... 2024 was the first year where iOS devices were exposed more than twice as much as Android devices."
Intel Agencies Warn of BadBazaar and MOONSHINE
And there's more! Cybersecurity and intelligence agencies from several countries (Australia, Canada, Germany, New Zealand, the UK, and the US) recently issued a joint advisory about attacks targeting Uyghur, Taiwanese, and Tibetan communities using malware like BadBazaar and MOONSHINE.
These attacks target NGOs, journalists, businesses, and civil society members who advocate for or represent these groups. The agencies warn that "The indiscriminate way this spyware is spread online also means there is a risk that infections could spread beyond intended victims."

A subset of app icons used by samples of the MOONSHINE surveillance tool as of January 2024
Both BadBazaar and MOONSHINE are trojans that steal sensitive data from Android and iOS devices, like locations, messages, photos, and files. They're often disguised as messaging, utility, or religious apps.
BadBazaar was first documented in November 2022, but campaigns have been ongoing since at least 2018. MOONSHINE was recently used by a group called Earth Minotaur to spy on Tibetans and Uyghurs.
The use of BadBazaar has been tied to