CrushFTP Under Attack CISA Urges Immediate Patching
Federal cybersecurity officials are sounding the alarm about a critical vulnerability in CrushFTP after evidence surfaced of hackers actively exploiting the flaw. The Cybersecurity and Infrastructure Security Agency (CISA) has added the vulnerability to its Known Exploited Vulnerabilities catalog, compelling federal agencies to patch immediately and urging all users to follow suit.

Heads up, folks! A critical security vulnerability in CrushFTP is now under active exploitation, meaning hackers are actively using it to break into systems. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added it to their Known Exploited Vulnerabilities (KEV) catalog, so it's serious business.
What's the Big Deal?
This vulnerability allows attackers to bypass authentication. In plain English, that means they can sneak into your CrushFTP server without needing a username or password! If successful, they could completely compromise your system. Good news is, it's fixed in versions 10.8.4 and 11.3.1, so update ASAP!
CISA puts it bluntly: "CrushFTP contains an authentication bypass vulnerability... potentially leading to a full compromise." Yikes!
The Confusing CVE Saga
This flaw is tracked as CVE-2025-31161 (with a scary 9.8 CVSS score). Interestingly, it was initially known as CVE-2025-2825, but that one's been rejected. It's a bit of a messy situation due to how different organizations assign CVE numbers.
Basically, Outpost24 responsibly reported the vulnerability to CrushFTP and requested a CVE. However, another group, VulnCheck, jumped the gun and released their own CVE before coordinating with CrushFTP or Outpost24.
How the Exploit Works (Simplified)
Want to know how attackers are pulling this off? Here's a simplified breakdown:
- They generate a random, long session token.
- They set cookies called "CrushAuth" and "currentAuth" with parts of that token.
- They send a special HTTP request with those cookies and a crafted "Authorization" header, pretending to be a user (like "crushadmin").
The result? They get authenticated as that user, gaining access to all their privileges.
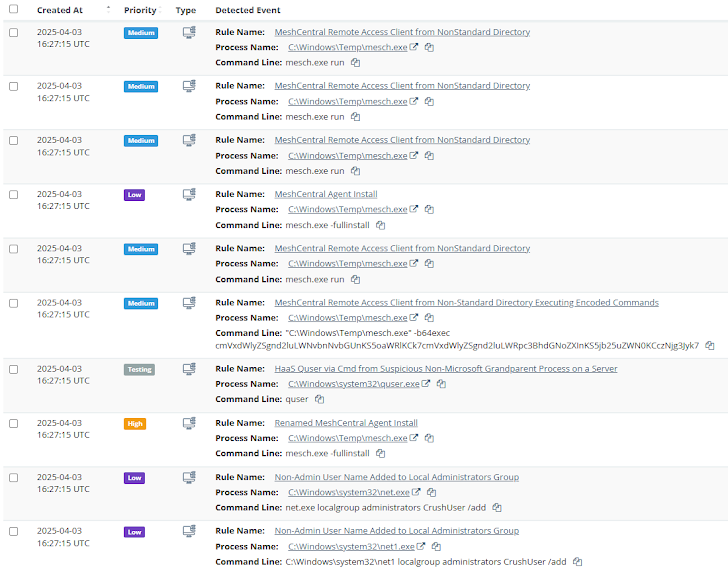
In the Wild: What Attackers Are Doing
Huntress has observed attackers actively exploiting this flaw since at least March 30, 2025. They've seen attackers install remote desktop software (like AnyDesk and MeshAgent) and even try to steal credentials.
In one case, after getting in, the attackers added a user called "CrushUser" to the administrator group and deployed a sneaky TgBot library, likely to collect data via a Telegram bot.
Numbers Don't Lie: Patch Now!
As of April 6, 2025, hundreds of CrushFTP instances remain unpatched. If you're running CrushFTP, especially if you're a Federal Civilian Executive Branch (FCEB) agency, you *need* to apply those patches by April 28th. Don't wait!




