Chinese Hackers Target ESET Users with Zero-Day Malware
A sophisticated Chinese hacking group is actively exploiting a previously unknown vulnerability in ESET security software to distribute a new, custom-built malware strain dubbed TCESB. The attacks, part of a broader campaign focused on Asian targets, demonstrate the group's ability to weaponize zero-day exploits and evade detection.

A Chinese hacking group, known for its activity in Asia, has been caught exploiting a flaw in ESET security software. They're using this vulnerability to deliver a brand-new piece of malware called TCESB.
Kaspersky researchers broke the news this week, stating that TCESB is designed to sneakily run malicious code while bypassing security tools. You can read their full analysis here.
This group, dubbed ToddyCat, has been active since at least December 2020, targeting various organizations in Asia.
Last year, Kaspersky reported on ToddyCat's use of sophisticated tools to maintain access to compromised systems and steal data on a massive scale from companies in the Asia-Pacific region.
How the Attack Works
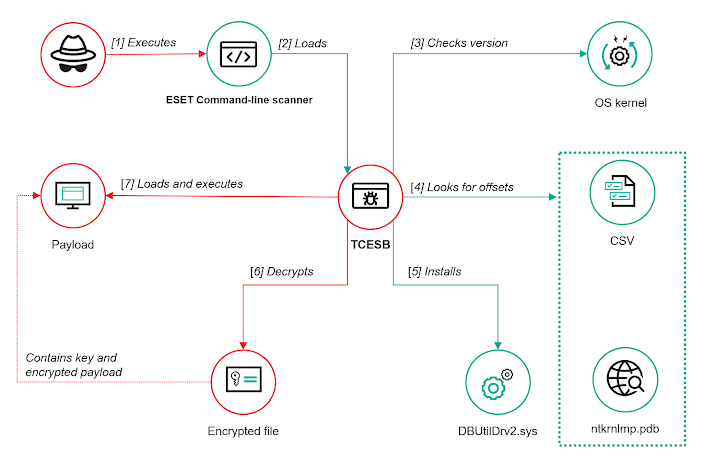
Earlier this year, Kaspersky's investigation into ToddyCat found a suspicious DLL file ("version.dll") lurking in the temp directories of multiple computers. This 64-bit DLL, named TCESB, is launched using a technique called DLL Search Order Hijacking. This allows the attackers to take control of the program's execution.
The attack takes advantage of a weakness in the ESET Command Line Scanner. The scanner insecurely loads a DLL ("version.dll") by first looking for it in the current directory *before* checking the system directories.
Now, "version.dll" is a legitimate Microsoft file, used for version checking and file installation. You'll usually find it in "C:\Windows\system32" or "C:\Windows\SysWOW64". More details on the legitimate file can be found here.
By exploiting this flaw, attackers can trick the system into running their *malicious* version of "version.dll" instead of the real one. ESET has since patched this vulnerability, which is tracked as CVE-2024-11859 (CVSS score: 6.8). The fix was released in late January 2025 after ESET was notified.
ESET explained in their advisory that this flaw could allow an attacker with administrator rights to load a malicious DLL and run its code. However, they emphasize that the attacker needs administrator privileges *already* for the attack to work.
The company stated that they've released updated versions of their Windows security products for consumers, businesses, and servers to address this vulnerability.
What Does TCESB Do?
TCESB is actually a modified version of an open-source tool called EDRSandBlast. It's designed to tamper with the operating system kernel to disable notification routines (also known as callbacks). These callbacks are supposed to alert drivers about important events, like when a new process is created or when a registry key is modified.
To make this happen, TCESB uses a technique called "bring your own vulnerable driver" (BYOVD). It installs a vulnerable Dell driver (DBUtilDrv2.sys) through the Device Manager. This driver has a known privilege escalation vulnerability, tracked as CVE-2021-36276.
This isn't the first time Dell drivers have been abused. Back in 2022, another Dell driver (dbutil_2_3.sys) had a similar vulnerability (CVE-2021-21551) that was exploited by the Lazarus Group (linked to North Korea) in BYOVD attacks to disable security measures.
Kaspersky researcher Andrey Gunkin explained that once the vulnerable driver is installed, TCESB continuously checks (every two seconds) for a payload file with a specific name in the current directory. The payload might not be present when the tool is first launched.
While the payload files themselves haven't been recovered, analysis shows they are encrypted using AES-128. They are decrypted and executed as soon as they appear in the expected location.
Staying Safe
Kaspersky recommends monitoring systems for driver installation events involving drivers with known vulnerabilities. They also suggest watching for events related to loading Windows kernel debug symbols on devices where kernel debugging isn't expected.




