Chinese Hackers Mustang Panda Upgrade Arsenal Targeting Myanmar
Mustang Panda, a hacking group with suspected ties to China, is sharpening its cyber espionage tools. A recent attack on an organization in Myanmar showcased the group's updated arsenal, including the StarProxy proxy tool, techniques to evade endpoint detection and response (EDR) systems, and enhancements to its TONESHELL malware.
Looks like the China-linked hacking group, Mustang Panda, has been busy. They've been linked to a cyber attack aimed at an organization in Myanmar, and they're packing some brand-new tools.
We're talking updated versions of their TONESHELL backdoor, a new tool for moving around networks called StarProxy, plus a couple of keyloggers (PAKLOG and CorKLOG), and even a driver – SplatCloak – that helps them sneak past Endpoint Detection and Response (EDR) systems. Sneaky!
Sudeep Singh, a researcher at Zscaler ThreatLabz, explained that the TONESHELL backdoor has been tweaked with changes to its communication methods. You can dive into the details in their two-part analysis here.
Mustang Panda – also known by a bunch of other names like BASIN and RedDelta – has been around since at least 2012. They're believed to be backed by the Chinese government.
Historically, they've gone after governments, the military, minority groups, and NGOs, mostly in East Asia, but sometimes in Europe too. They're known for using DLL side-loading tricks to spread the PlugX malware.
But, since late 2022, they've increasingly relied on their own custom malware, TONESHELL, to deliver the next stage of their attacks.
Zscaler researchers have found three new versions of TONESHELL, each a bit more sophisticated than the last:
- Variant 1: Your basic reverse shell.
- Variant 2: Can download DLL files from the attackers and inject them into legitimate processes, like svchost.exe.
- Variant 3: Can download files and run commands received from a remote server using a custom protocol.
Then there's StarProxy, the new tool mentioned earlier. It's launched via DLL side-loading and uses a "FakeTLS" protocol to proxy traffic and help the attackers communicate without being detected.
According to Singh, StarProxy lets the hackers bounce traffic between infected machines and their command-and-control (C2) servers, encrypting everything with a custom XOR-based algorithm.
The tool also uses command-line arguments to specify the IP address and port for communication, allowing attackers to relay data through compromised machines.
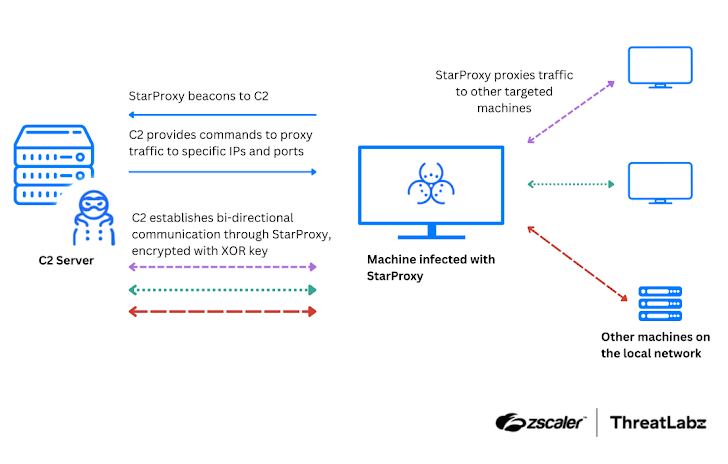
The idea behind StarProxy seems to be to access internal workstations that aren't directly connected to the internet.
The keyloggers, PAKLOG and CorKLOG, do what you'd expect: steal keystrokes and clipboard data. CorKLOG is a bit more advanced, encrypting the stolen data and using services or scheduled tasks to stay persistent on the system.
Interestingly, neither keylogger can send the stolen data back to the attackers on its own. They just collect the data, meaning Mustang Panda needs other tools to actually exfiltrate the information.
Finally, there's SplatCloak, a driver designed to disable security features in Windows Defender and Kaspersky, helping the malware stay hidden.
Singh sums it up: "Mustang Panda demonstrates a calculated approach. Continuous updates, new tooling, and layered obfuscation prolongs the group's operational security and improves the efficacy of attacks."
UNC5221 Unleashes New BRICKSTORM Malware on Windows
In related news, cybersecurity firm NVISO has linked the China-nexus cyber espionage group UNC5221 to a new version of the BRICKSTORM malware, targeting Windows systems in Europe since at least 2022. You can read more here.
BRICKSTORM was first documented last year in connection with the Ivanti Connect Secure zero-day exploits (CVE-2023-46805 and CVE-2024-21887) that targeted MITRE Corporation. It's a Golang backdoor that typically runs on Linux servers running VMware vCenter.
According to Google Mandiant, BRICKSTORM can act as a web server, manipulate files and directories, upload/download files, run shell commands, and perform SOCKS relaying. It communicates over WebSockets to a hard-coded C2 server. More details are available here.
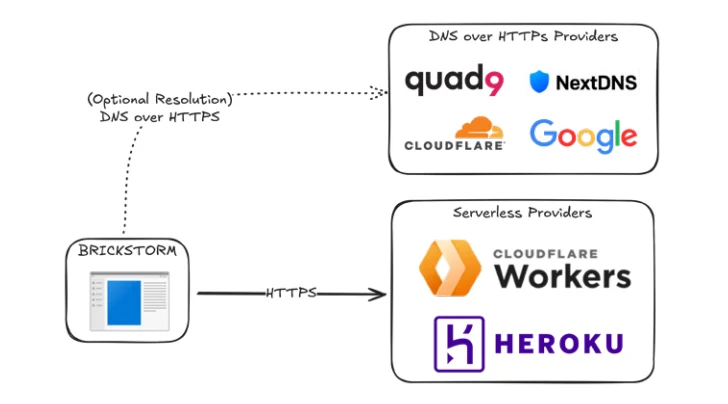
The new Windows versions of BRICKSTORM, also written in Go, give attackers a file manager and network tunneling capabilities through a control panel. This lets them browse the file system, create/delete files, and tunnel network connections for moving around the network.
They also use DNS-over-HTTPS (DoH) to find their C2 servers, which helps them avoid detection by network defenses.
NVISO notes that the Windows samples don't have command execution capabilities. Instead, the attackers have been observed using network tunneling along with valid credentials to abuse protocols like RDP or SMB.