Chinese Hackers Deploy SNOWLIGHT Malware Against Linux Servers
A hacking group with suspected ties to China, tracked as UNC5174, is actively targeting Linux servers with a sophisticated malware campaign. Security researchers have uncovered the group's use of a modified version of the SNOWLIGHT malware, along with a previously unknown open-source tool called VShell, to compromise systems.

Chinese Hackers Target Linux Systems with New Malware
A hacking group with suspected ties to China, known as UNC5174, is making headlines with a new campaign targeting Linux systems. They're using a revamped version of the SNOWLIGHT malware and a fresh, open-source tool called VShell to compromise machines.
According to Sysdig researcher Alessandra Rizzo, these threat actors are increasingly turning to open-source tools. Why? It's cost-effective and helps them blend in. "It saves money and, in this case, plausibly blend in with the pool of non-state-sponsored and often less technical adversaries (e.g., script kiddies), thereby making attribution even more difficult," Rizzo explained.
It seems this particular group, UNC5174, has been flying under the radar for the past year, despite being linked to the Chinese government.
Previously, Google's Mandiant reported that UNC5174 (also called Uteus or Uetus) was exploiting vulnerabilities in Connectwise ScreenConnect and F5 BIG-IP. Their weapon of choice? SNOWLIGHT, a C-based ELF downloader that grabs another piece of malware called GOHEAVY from servers using the SUPERSHELL command-and-control framework.
But that's not all. They've also been using GOREVERSE, a publicly available reverse shell backdoor written in Golang, operating through SSH.
The French National Agency for the Security of Information Systems (ANSSI) noted similar tactics in their 2024 Cyber Threat Overview report. They saw an attacker using the same playbook as UNC5174, exploiting Ivanti Cloud Service Appliance (CSA) flaws like CVE-2024-8963, CVE-2024-9380, and CVE-2024-8190 to gain control and run code.
"Moderately sophisticated and discreet, this intrusion set is characterized by the use of intrusion tools largely available as open source and by the – already publicly reported – use of a rootkit code," ANSSI stated.
Interestingly, SNOWLIGHT and VShell can also target macOS systems. VShell was even disguised as a fake Cloudflare authenticator app, distributed in an attack chain that's still under investigation. An analysis of files uploaded to VirusTotal from China in October 2024 revealed this tactic.
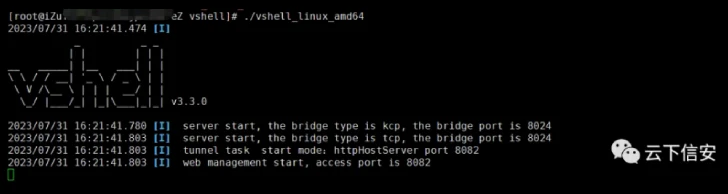
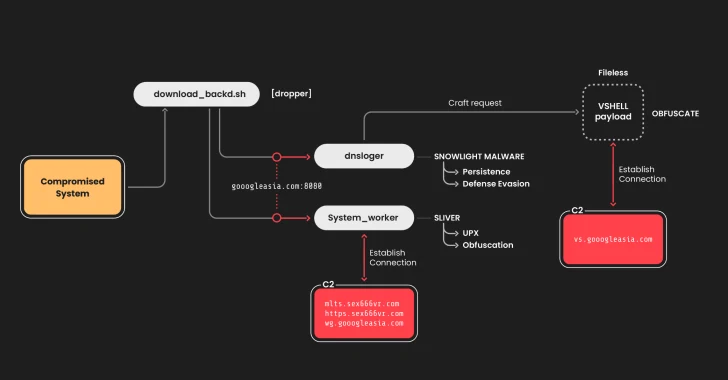
In late January 2025, Sysdig observed SNOWLIGHT dropping a fileless, in-memory payload called VShell. This remote access trojan (RAT) is a favorite among Chinese-speaking cybercriminals. The initial entry point for these attacks remains a mystery.
The attack starts with a malicious bash script ("download_backd.sh") that launches two programs associated with SNOWLIGHT (dnsloger) and Sliver (system_worker). These tools ensure the malware stays put and can communicate with a command-and-control (C2) server.
The final step involves SNOWLIGHT delivering VShell through a specially crafted request to the C2 server. This gives the attackers remote control and allows them to further exploit the compromised system.
"[VShell] acts as a RAT (Remote Access Trojan), allowing its abusers to execute arbitrary commands and download or upload files," Rizzo explained. Sysdig warns that "SNOWLIGHT and VShell pose a significant risk to organizations due to their stealthy and sophisticated techniques," particularly their use of WebSockets for command-and-control and the fileless nature of the VShell payload.
Around the same time, TeamT5 revealed that another China-linked hacking group likely exploited flaws in Ivanti appliances (CVE-2025-0282 and CVE-2025-22457) to gain access and deploy the SPAWNCHIMERA malware.
According to the Taiwanese cybersecurity firm, these attacks targeted a wide range of sectors in almost 20 countries, including Austria, Australia, France, Spain, Japan, South Korea, the Netherlands, Singapore, Taiwan, the United Arab Emirates, the United Kingdom, and the United States.
These findings also align with accusations from China that the U.S. National Security Agency (NSA) launched "advanced" cyber attacks during the Asian Winter Games in February. They specifically accused three NSA agents of repeatedly attacking China's critical information infrastructure and Huawei.
"At the ninth Asian Winter Games, the U.S. government conducted cyberattacks on the information systems of the Games and the critical information infrastructure in Heilongjiang," Foreign Ministry Spokesperson Lin Jian stated. "This move is egregious for it severely endangers the security of China's critical information infrastructure, national defense, finance, society, and production as well as its citizens' personal information."