Amazon Fixes EC2 Agent Bug That Allowed Privilege Escalation
A security vulnerability in Amazon's EC2 Simple Systems Manager (SSM) Agent has been patched, averting potential attacks where malicious actors could have elevated their system privileges and executed arbitrary code. Security researchers uncovered the path traversal flaw, prompting Amazon to release a fix.
Heads up, AWS users! Cybersecurity researchers recently uncovered a security vulnerability in the Amazon EC2 Simple Systems Manager (SSM) Agent. The good news? It's already been patched. But here's what you need to know.
This flaw, if exploited, could have allowed attackers to gain elevated privileges and even execute code on your systems. Imagine someone being able to create directories where they shouldn't, run scripts as root, and potentially escalate privileges to wreak havoc. Not good!
Cymulate, a cybersecurity firm, broke down the details in a report. They explained how attackers could write files to sensitive areas, leading to all sorts of malicious activities.
What is Amazon SSM Agent Anyway?
So, what exactly is this SSM Agent? Well, Amazon SSM Agent is like a remote control for your EC2 instances and on-premises servers. It allows administrators to manage, configure, and run commands on these machines from a central location.
Think of it this way: it processes commands and tasks defined in SSM Documents. These documents contain plugins, each designed for specific tasks like running scripts or automating deployments.
Here's where things get interesting: the SSM Agent dynamically creates directories and files based on these plugin specifications, using plugin IDs as part of the directory structure. And that's where the weakness crept in.
The Path Traversal Problem
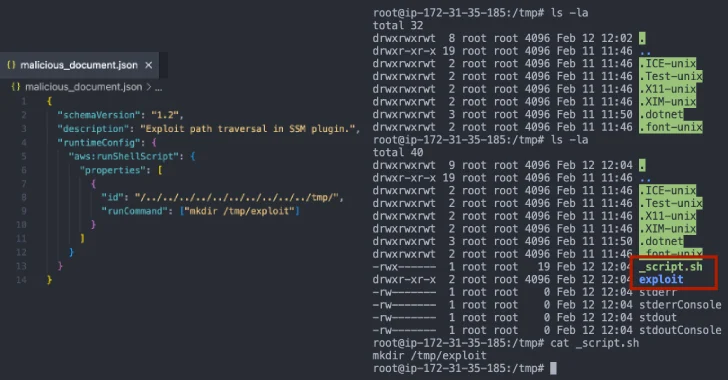
The issue discovered by Cymulate? A path traversal vulnerability. It all boiled down to improper validation of plugin IDs. Basically, attackers could manipulate the filesystem and execute code with elevated privileges because of a flaw in the "ValidatePluginId" function within pluginutil.go.
Elad Beber, a security researcher, explained that this function didn't properly sanitize input. This allowed attackers to use malicious plugin IDs containing path traversal sequences (like "../") to navigate the file system in unintended ways.
In simple terms, an attacker could create a specially crafted plugin ID when creating an SSM document (something like "../../../../../../malicious_directory") to run commands or scripts on the system, leading to privilege escalation.
The Fix is In!
Thankfully, the vulnerability has been addressed. After Cymulate responsibly disclosed the issue on February 12, 2025, Amazon released version 3.3.1957.0 of the Amazon SSM Agent on March 5, 2025.
According to the release notes, the update includes a "BuildSafePath" method to prevent path traversal in the orchestration directory. So, make sure you're running the latest version to stay protected!




