Agent Tesla and XLoader Delivered in Sophisticated JSE PowerShell Attack
Cybersecurity researchers have uncovered a complex, multi-stage malware campaign leveraging .JSE files and PowerShell to distribute notorious malware such as Agent Tesla, Remcos RAT, and XLoader. The attack's layered approach suggests a significant effort to evade detection.
A sneaky new attack is making the rounds, using a multi-stage approach to deliver some nasty malware like Agent Tesla, Remcos RAT, and XLoader. Think of it like a set of dominoes, each one carefully placed to knock down the next, ultimately leading to a malware infection.
Saqib Khanzada, a researcher at Palo Alto Networks Unit 42, explains that these complex methods are becoming more common. Attackers are trying to slip past security measures like sandboxes to make sure their malicious payloads actually get delivered and run.
So, how does this particular attack work? It starts with a phishing email. You know the kind – something that looks legitimate but is designed to trick you.
The Phishing Hook
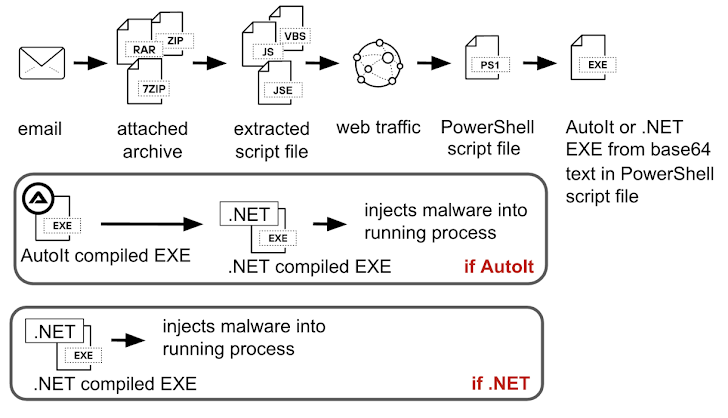
This phishing email contains a 7-zip archive attachment, which might sound harmless, but it holds a JavaScript encoded (.JSE) file. Opening this file is where the trouble really begins.
These emails were spotted in December 2024 and often pretend to be order confirmations. The email might say a payment has been made and ask you to open the attached file to view the order details. If you launch the JavaScript file, it kicks off a chain reaction, downloading a PowerShell script from a remote server.
That PowerShell script contains a Base64-encoded payload. This payload is then decoded, saved to your Windows temporary directory, and executed. And here's where it gets even more interesting...
The Next Stage Dropper
The attack uses a next-stage dropper, which can be compiled using either .NET or AutoIt.
If it's a .NET executable, it decrypts an embedded payload (likely a variant of Agent Tesla, possibly Snake Keylogger or XLoader). This decrypted code is then injected into a running "RegAsm.exe" process – a trick seen in previous Agent Tesla attacks.
If the executable is compiled with AutoIt, it adds another layer of complexity. The AutoIt script contains an encrypted payload that loads the final shellcode. This shellcode causes the .NET file to be injected into a "RegSvcs.exe" process, ultimately leading to the deployment of Agent Tesla.
Khanzada points out that using multiple execution paths makes the attack more resilient and harder to detect. The focus isn't necessarily on using super-advanced techniques, but on creating a complex, multi-layered attack.
Essentially, by stacking relatively simple stages, attackers can build attack chains that are surprisingly difficult to analyze and stop.
Another Threat: IronHusky and MysterySnail RAT
Separately, Kaspersky revealed a campaign targeting government organizations in Mongolia and Russia. This campaign involves a new version of a malware called MysterySnail RAT, and it's linked to a Chinese-speaking group known as IronHusky.
IronHusky has been active since at least 2017. They were previously identified in connection with the exploitation of a Windows privilege escalation flaw (CVE-2021-40449) to deliver MysterySnail.
The current infections start with a malicious Microsoft Management Console (MMC) script disguised as a Word document from the National Land Agency of Mongolia. This script retrieves a ZIP archive containing a decoy document, a legitimate binary ("CiscoCollabHost.exe"), and a malicious DLL ("CiscoSparkLauncher.dll").
The exact method used to distribute the MMC script isn't clear, but the lure document suggests it may be delivered via a phishing campaign.
As seen in other attacks, "CiscoCollabHost.exe" is used to sideload the malicious DLL. This DLL acts as an intermediary backdoor, communicating with attacker-controlled servers using the open-source piping-server project.
The backdoor can run command shells, download/upload files, list directory contents, delete files, create new processes, and terminate itself. These capabilities are then used to sideload the MysterySnail RAT.
This latest version of MysterySnail can accept nearly 40 commands, allowing it to manage files, execute commands via cmd.exe, spawn and kill processes, manage services, and connect to network resources using dedicated DLL modules.
Kaspersky noted that after some of the affected companies took steps to block the intrusions, the attackers dropped a "repurposed and more lightweight version" of MysterySnail, called MysteryMonoSnail.
"This version doesn't have as many features as the full MysterySnail RAT," Kaspersky explained. "It's designed with only 13 basic commands for listing directory contents, writing data to files, and launching processes and remote shells."